

2022/01/31 Microsoft Cloud Solutions 967 visit(s)
Ctelecoms

Now that enterprises are giving more attention to security matters and data privacy, major technology providers are working non-stop to provide solutions that can make sure that the workflow in your organization is moving uninterrupted.
Microsoft has announced that threat and vulnerability management support in Microsoft Defender for Endpoint is now generally available across all platforms, with the latest edition of Android and iOS.
This solution will allow organizations around the world to discover, manage, prioritize, block and remediate vulnerabilities in real-time.
Let’s dive in to the details of this announcement.
The Microsoft Defender for Endpoints will now support “all major device platforms across the organization – spanning workstations, servers, and mobile devices” according to Microsoft.
So, now after generalizing to “all major device platforms” what are those platforms really?
We’ll the latest update Microsoft just added Android and iOS support to the existing support for macOS and Windows devices.
Of course, Microsoft already provided support for Linux server distros too, however, Linux client support is still not available till this moment.
It’s smart not to bargain in terms of security, especially now where enterprises are adopting remote work more than ever before.
Microsoft Defender for Endpoints will now provide vulnerability management capabilities for iOS and Android devices as part of its new mobile threat defense solution.
Clients now are able to identify the security threats that pose a major risk to their company, not to mention that this solution, in particular, facilitates collaboration between IT administrators and security teams and experts on resolving cyber security issues.
According to Microsoft, the new release enables enterprise customers to conduct a vulnerability assessment of Android OS versions and applications on all enrolled Android devices. However, it won’t assess the vulnerability for applications in “bring your own device” Android scenarios, but IT experts with administrative privileges can still enable this capability.
As for iOS, vulnerability assessment is currently only available to check OS versions, and in a later update, it will be available to support applications as well.
Now and to get started, IT administrators need to head to the Microsoft Defender Security Center and select Threat & Vulnerability Managemnt.
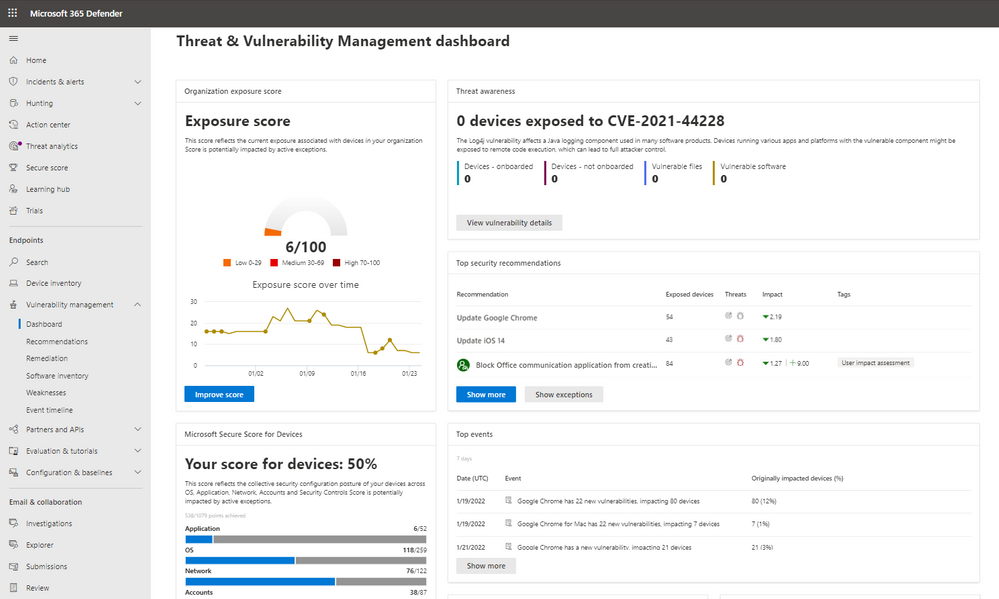
Vulnerability managemnt dashboard provides quick access to insights across devices, and IT admins can check the exposure level of all enrolled mobile devices in the Device Inventory section.
Even though the new relase doesn’t support applications yet, Microsoft has launched for iOS users zero-touch onboarding support in public preview. After configuration, the application will be installed automatically on iPhones and iPads without anu user interaction.
This update helps enterprise admins in securing remote iOS devices at the endpoint.
Microsoft Defender for Endpoints was reorganized recently by Microsoft into two products, Plan 1 and Plan 2.
The new Plan 1 product was designed for organizations that are looking just for device protection capabilities and was commercially released in November to be expected to show up sometime this year for organizations having M354 E3/A3 subscriptions.
Ctelecoms is a proud Microsoft partner, working to get the full advantage of this partnership to serve customers in Saudi Arabia.
If you’re thinking of this solution and finding it complicated, just reach out to our team on: https://www.ctelecoms.com.sa/en/Form15/Contact-Us