Now more than ever before, business leaders and decision makers across Saudi Arabia are facing new waves of security and productivity challenges. In order to succeed in keeping their business productive and secure in such a remote work era, they must be flexible and adapt quickly to new challenges and uncertainties.
Level Up Your Remote Workforce Productivity & Security Using Microsoft 365 Business Premium
Microsoft 365 Business Premium is an integrated solution that helps your employees stay productive, secure and connected from anywhere. Microsoft 365 Business Premium simplifies the process of delivering security and management with employees working from home.
Here's how Microsoft 365 Busienss Premium Does Wonders For Your Remote Workers:
1. Secure Access, Device & Data with Microsoft 365 Business Premium
M365 Business Premium helps you enable a seamless productivity experience for your employees who are trying to access business resources from their homes. At this stage, we recommend that you approach security in terms of Securing Access, Securing Devices (PCs, Macs & Mobile Devices) and Securing Data. Microsoft 365 Business Premium provides a solid foundation of security features across these three categories. Here’s how:
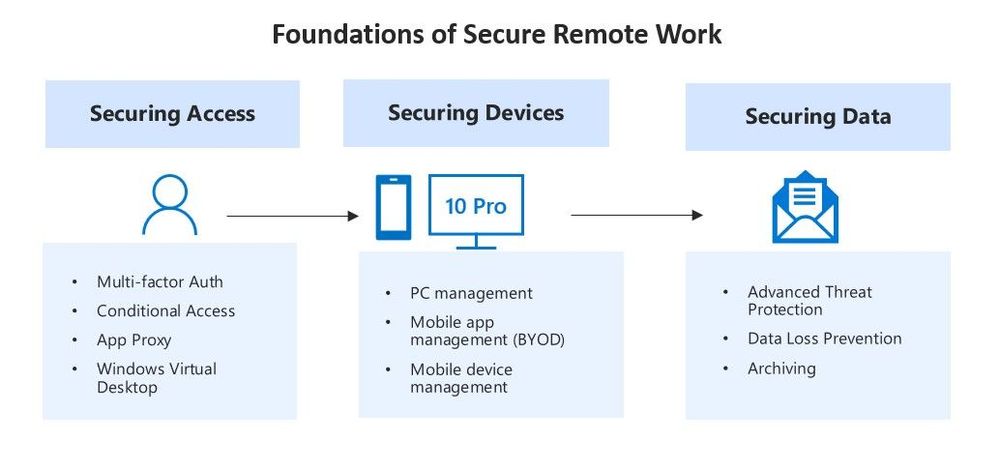
1. Securing Access:
One of the most important aspects of enabling work from home scenarios is making sure users can access systems remotely in a secure manner - from anywhere and any device. The following features in Microsoft 365 Business Premium help you do exactly that. You can enable some of them or all of them based on the needs of your organization:
- Multi-Factor Authentication (MFA): This enhances security by requiring more than one method of authentication to verify the user's identity when they log in to your company’s systems or data. For example, the user must put in a code or answer a phone call, apart from logging in with their username and password. This additional level of verification ensures that non-employees cannot gain access to your environment even if the user’s username and password are compromised - for example, in a phishing attack. Learn more about setting up MFA
- Conditional Access: This feature helps you control access to your environment based on location, app, device state and user state. For example, you could create a policy that blocks access when someone attempts to log in from a country in which you don’t do business Or, you could use conditional access to restrict access if a user is logging in from an unrecognized and potentially compromised device. Conditional Access gives you the ability to safeguard access based on multiple criteria rather than simply relying on a username and password.
- Azure AD Application Proxy: Many companies have business-critical apps running on-premises, which aren’t accessible from outside the corporate network. Azure AD App Proxy allows you to publish these applications externally. It is a lightweight agent that enables internet access to your on-premises apps, without opening broad access to your network. Learn more about enabling Azure AD App Proxy
- Windows Virtual Desktop (WVD): If you have apps with sensitive information such as medical or financial information and you want to make sure that data is securely accessed by users working from home, you can easily enable this scenario by utilizing WVD. WVD creates a virtual desktop for users to access remotely. Employees can only access that information in that remote virtualized session and are unable to save any data on their local workstations. Learn more about WVD in this Microsoft Mechanics Video
2. Securing Devices:
Employees are using a wide array of laptops, desktops & mobile devices to access company data and get work done during this time. The challenge is keeping all these devices secure as people use them to work with sensitive business information. Microsoft Intune is included in Microsoft 365 Business Premium and can help you manage your PCs and mobile devices. Here’s how:
- Managing PCs with Intune: To maintain security, employees need to keep their work devices up to date with latest security updates while they are outside your corporate network. Intune can not only help keep those devices up to date, but also help you fully manage your PCs with features such as enforcing security policies or wiping data from devices remotely. In Microsoft 365 Business Premium, you can apply pre-configured device policies for Windows 10 PCs accessing your environment, such as enabling Microsoft Defender AV and enabling ransomware protection for critical folders.
- Managing Mobile Devices with Intune: Intune also helps you manage mobile devices and gives you flexibility on how much control you want to exert on mobile devices accessing your company environment. In a Bring-You-Own-Devices (BYOD) situation where employees are using personal mobile devices, you may not want full control of a user’ personal device but may still want to secure the company data that the user is accessing. In this case you can use Intune app protection policies to secure company data (Email, Teams, and OneDrive) on the device. However, if you want full control of a user’s mobile device, you can “enroll” a device into Intune Mobile Device Management and fully control the device settings and set the security policies.
- Intune App protection Policies: These policies allow you to restrict users from copying, pasting, or saving corporate data and documents from Office mobile apps to personal apps or storage locations—without requiring any kind of device enrollment. For example, with these policies in place, a user cannot save a spreadsheet of customer data to their personal files. Because corporate data is kept within approved apps and locations, if a personal device is lost or stolen, you can selectively wipe this information without affecting personal photos, apps, and data. These policies are easily activated through the Microsoft 365 Business Premium administration console.
- Intune Mobile Device Management: If you want to enforce stronger mobile device policies that go beyond App Protection Policies, you can enable full mobile device management capabilities in Intune. Then you can enforce deep, device-centric security policies such as blocking screen capture. This approach requires a device enrollment process for iOS or Android devices.
3. Securing Data:
Another important step in enabling remote work scenarios is ensuring that company data is protected. As cybercriminals adjust their tactics to take advantage of the current situation, it is prudent to enable policies to defend against cyber threats and prevent phishing. It is also imperative to ensure sensitive data like social security numbers, customer credit card information, and personal identifiable information (PII) are protected and that policies are in place to control access as well as sharing.
- Office 365 Advanced Threat Protection: Office 365 ATP helps guard your business against sophisticated phishing and ransomware attacks across email, OneDrive & Teams that are intended to compromise employee or customer information. Office 365 ATP protects you in the following ways:
- Sophisticated attachment scanning in email, OneDrive & Teams that uses AI-powered analysis to detect and discard dangerous messages
- Automatic checks of links in email, documents & Teams to assess if they are part of a phishing scheme and prevent users from accessing unsafe websites
- Anti-spoofing intelligence to warn you against domain impersonation intended to trick users in to thinking that the email is coming from an entity inside the organization. You can learn more about enabling Office 365 ATP features here.
- Data Loss Prevention (DLP): If you are worried about an increased risk of employees sharing sensitive information by mistake when working from home, this feature helps you identify, monitor, and protect sensitive information from being unintentionally shared either through email or in documents. DLP detects specific types of sensitive information being communicated to people outside your organization, such as credit card numbers, government-issued identifiers, dates of birth and even locale-specific personally identifiable information (PII).
- Exchange Online Archiving: This helps keep all company data safe, preserved in the event of lost/ stolen devices, infrastructure failure or to meet litigation and compliance obligations. Exchange Online Archiving safeguards data by allowing messages and documents to be easily archived and then accessed anytime/anywhere. It preserves user information including deleted items for electronic discovery or restoration at a later date. Learn more about setting up data retention policies.
Whether you are continuing your journey to secure a remote workforce or are just getting started, Ctelecoms, Gold-Certified Microsoft Partner in KSA, can help you simplify the process of delivering security and management for your remote workers. Get started with Microsoft 365 Business Premium today!
Credit: Microsoft Tech Community



