

2024/04/14 IT & Cyber-Security Solutions 177 visit(s) 8 min to read
Ctelecoms

Cisco Identity Services Engine (ISE) stands as a cutting-edge platform for identity management, access control, and policy implementation, empowering enterprises to enforce regulatory compliance, bolster infrastructure security, and optimize service operations. The distinctive architecture of Cisco ISE facilitates the real-time collection of contextual data from networks, users, and devices.
This wealth of information allows administrators to proactively make governance decisions by associating identities with diverse network elements, including access switches, wireless LAN controllers (WLCs), virtual private network (VPN) gateways, and data center switches. Cisco ISE plays a pivotal role in the comprehensive Cisco Security Group Access Solution.
What is Cisco Identity Services Engine (ISE)?
In straightforward terms, Cisco ISE is a network management solution that provides control over who can access your network and dictates their level of access. It handles authentication for wired, wireless, and VPN users, boasting scalability to accommodate millions of endpoints.
Cisco ISE functions as a network administration tool, facilitating the establishment and enforcement of security and access policies for endpoint devices linked to the company's network administrator devices, such as routers and switches. The primary goal is to streamline identity management across a variety of devices and applications.
The Policy Administration Node (PAN) serves as the focal point where administrators log in to set up policies and implement changes across the entire ISE system. Once configured on the PAN, these changes are disseminated to the policy services nodes. The PAN is responsible for managing all system-related configurations and can be set up in various modes, including standalone, primary, or secondary configurations.
The Monitoring Node (MnT) functions as the central hub for collecting logs and generating reports within the ISE system. It serves as the repository for all events taking place in the ISE topology. Every occurrence is logged on the monitoring node, allowing administrators to generate reports that provide insights into the current status of connected devices and unidentified devices on the network.
The Policy Services Node (PSN) serves as the entry point into the network. Each switch is set up to inquire with a RADIUS server for the policy decision that should be applied to the network port; this RADIUS server is essentially the PSN. In more extensive deployments, multiple PSNs are employed to distribute the load of network requests effectively. The PSN is responsible for delivering a range of services, including network access, posture assessment, guest access, client provisioning, and profiling. In a distributed setup, it is essential to have at least one PSN.
Depending on the size of your deployment all three personas can be run on the same device or spread across multiple devices for redundancy.
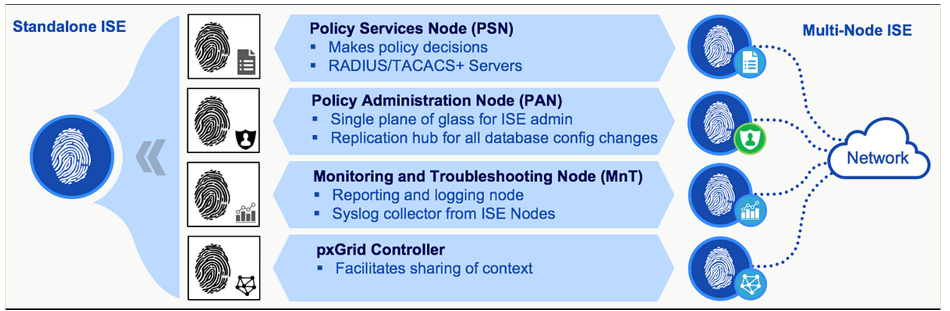
ISE deployment offers flexibility, with the option to install it on either a physical appliance or a Virtual Machine. This facilitates the establishment and enforcement of access policies for endpoint devices connected to a company's network.
Physical appliance: SNS 3400(EOL), SNS 3500, SNS 3600
Virtual: ISE can be installed on VMware, Hyper-V
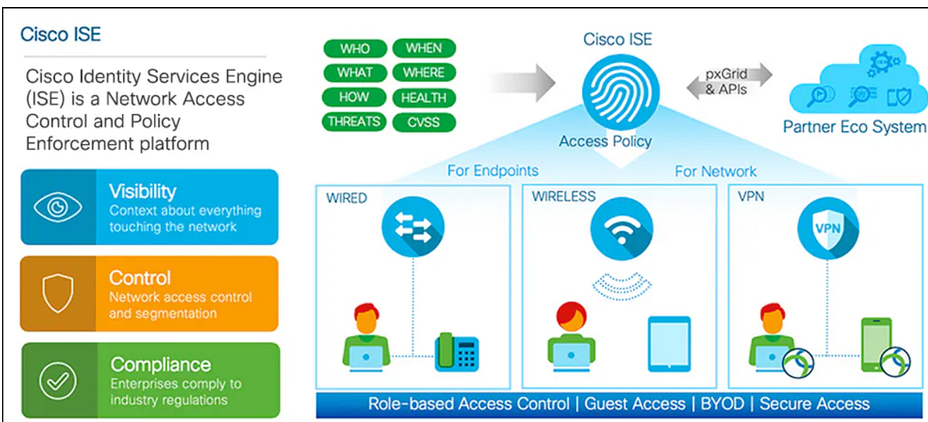
The main objective of Cisco ISE is to validate wired or wireless users seeking access to the network or attempting device administration. Each user is authenticated against the server to determine permission levels. Based on the validation outcome, the user is granted specific access to the network or device. Cisco ISE essentially ensures secure and authorized access for users in line with predefined policies.
Standalone Deployment: In a standalone deployment, a single Cisco ISE node is utilized, encompassing the Administration, Policy Service, and Monitoring personas. This configuration is suitable for small production setups or laboratory environments. However, it lacks redundancy since only one node is in operation.
Hybrid Deployment: A hybrid deployment involves multiple ISE nodes, with the Policy Administration Node (PAN) and Monitoring (MNT) personas coexisting on a single node. This node functions as both PAN and MNT, and additional Policy Service Nodes (PSNs) can be added to the deployment. Hybrid deployments offer a balance between redundancy and resource utilization.
Distributed Deployment: A distributed deployment comprises multiple ISE nodes, each dedicated to a specific persona. This setup includes a Primary Administration ISE node, Secondary Administration nodes, Primary Monitoring node, Secondary Monitoring node, and PSNs (Policy Service Nodes).
Each node can perform one or multiple services, allowing for scalability and fault tolerance. Distributed deployments are commonly used in larger, enterprise-level implementations, ensuring optimal performance and high availability.
Cisco ISE operates as a policy-based network access control solution, providing the flexibility of managing various network access scenarios, including wireless, wired, guest, and client provisioning, through the use of policy sets.
Upon installation, ISE comes with a default policy set already defined. This default policy set encompasses predefined authentication, authorization, and exception policy rules. It serves as a foundational framework, streamlining the initial configuration process. Policy sets in ISE are instrumental in shaping and enforcing network access policies across different use cases, offering a structured approach to managing access control.
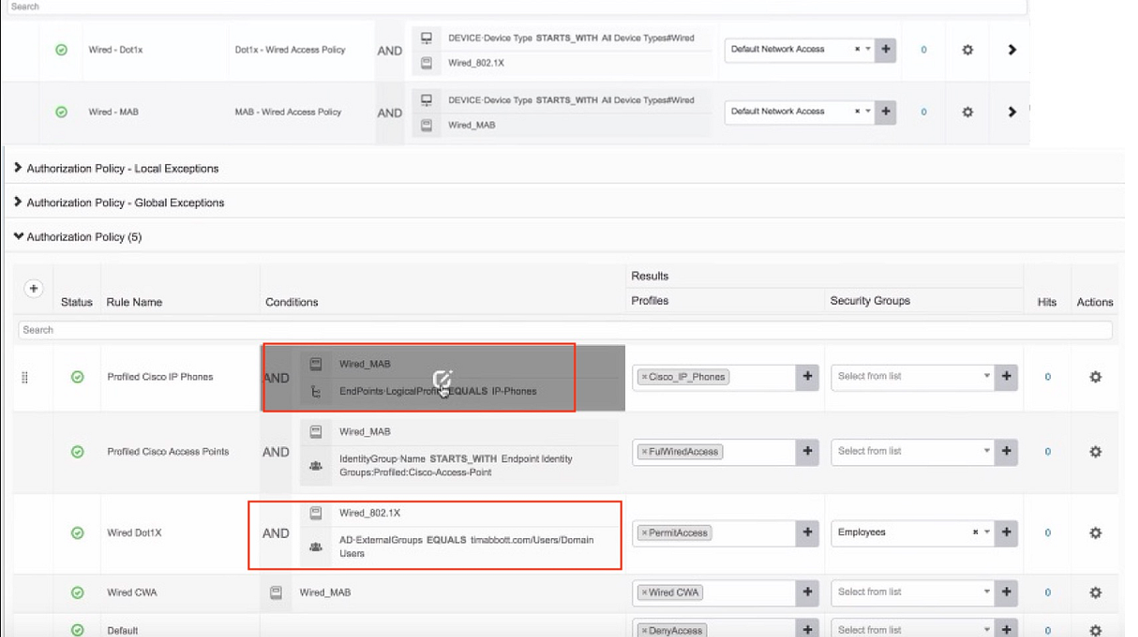
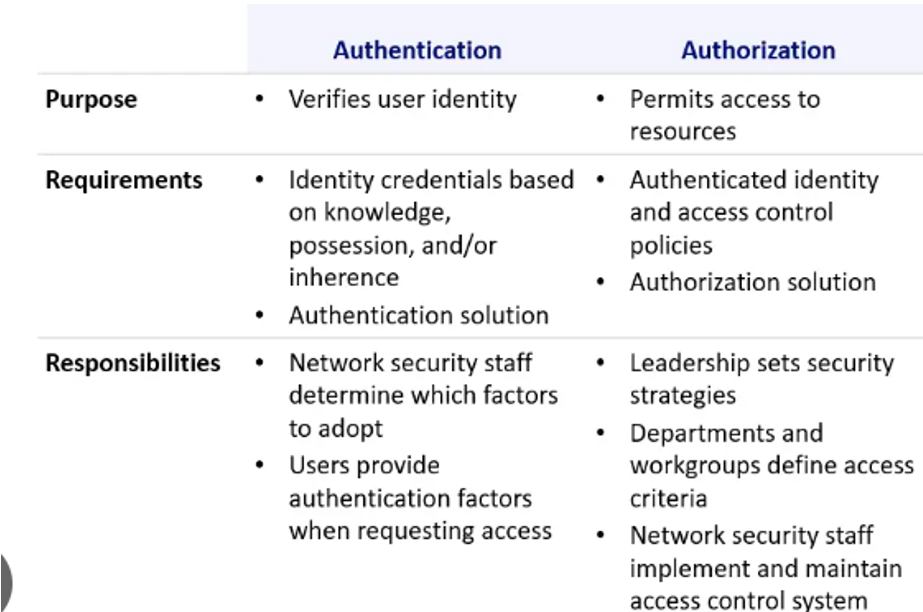
Authentication: In the authentication process, the focus is on verifying the presence of the user in the identity store and validating the credentials provided by the user. This includes checking the type of traffic, such as whether it is wired or wireless, and specifying the identity store to be consulted for this traffic. Essentially, authentication ensures that the user is who they claim to be and that their provided credentials are valid.
Authorization: On the other hand, authorization involves fetching various attributes for the user and determining which resources the user has access to. Authorization policies can consist of single or multiple user-defined conditions. These conditions, often following an If-Then convention, link entered values for identity groups with specific attributes or conditions, creating a unique authorization profile. In simpler terms, authorization defines what actions or resources a user is allowed to access based on their identity and other specified conditions.
RADIUS: Remote Access Dial-In User Service (RADIUS) is an open standard protocol used for the communication between any vendor AAA client and ACS/ISE server. The standard ports used for radius communication are 1812 for authentication and 1813 for accounting. Legacy radius port number are 1645 for authentication and 1646 for accounting.
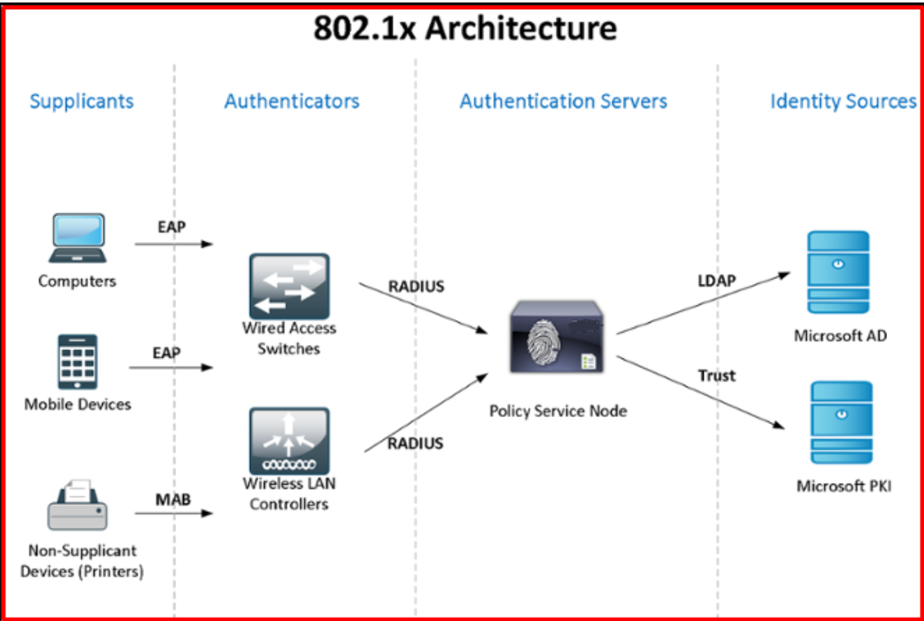
802.1X is a protocol that establishes client-server-based access control and authentication, designed to prevent unauthorized clients from connecting to a Local Area Network (LAN) through publicly accessible ports. The fundamental principle is that access is denied to the end client until proper authorization is granted.
During the authentication process, 802.1X access control permits only Extensible Authentication Protocol over LAN (EAPOL) traffic through the port to which the client is connected. This means that until the client is successfully authenticated, only specific authentication-related traffic is allowed. Once authentication is completed successfully, the port opens up, allowing normal traffic to pass through. Essentially, 802.1X ensures a secure and controlled access mechanism for devices connecting to a network.
You can use Cisco pxGrid to share the context-sensitive information from Cisco ISE session directory with other network systems such as ISE Eco system partner systems and other Cisco platforms. The pxGrid framework can also be used to exchange policy and configuration data between nodes like sharing tags and policy objects between Cisco ISE and third-party vendors, and for other information exchanges. Cisco pxGrid also allows third party systems to invoke adaptive network control actions.”
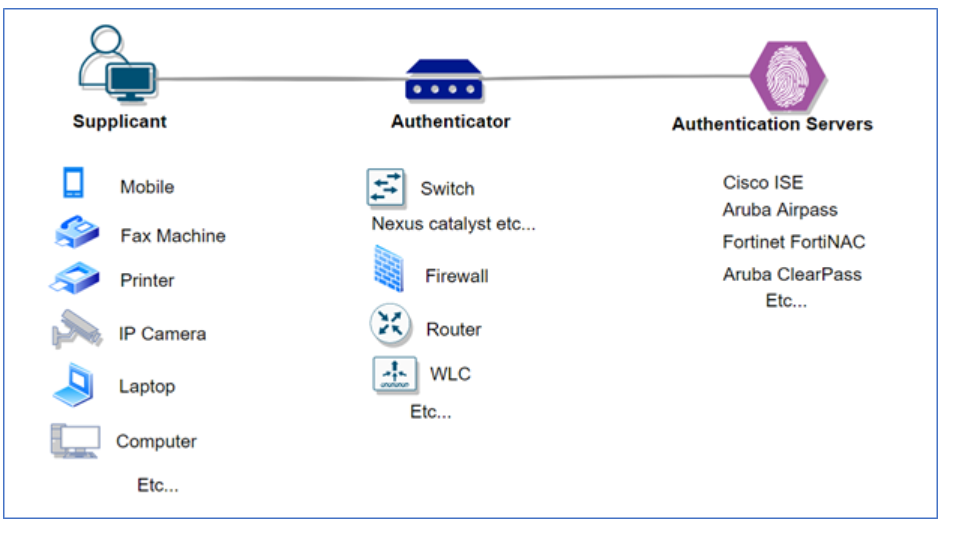
Supplicant, Network Access Device and Authentication Server are the 3 key components which are involved in dot1x authentication.
Supplicant: User/Endpoint who’s trying to authenticate in order to gain the network access.
NAD: Access switch/Access point to which the supplicant is connected which will carry the user credentials and present it to the server in order to authenticate the user.
Authentication Server: Credential’s which were presented by NAD will be verified on the server and depending on the end result either access will be given or denied.
Our Cisco ISE node (appliance) can provide a number of services to the network, depending on persona’s enabled.
The persona nodes available on Cisco ISE nodes are:
We’ll start by looing at the policy administration node (PAN). The PAN persona is used by the administrator to login and configure the ISE deployment.
Any configuration made to our ISE deployment will be made on the node with the PAN persona enabled. This node then pushes configuration changes from the PAN to the other nodes within the deployment.
The PAN can be deployed within the following methods, depending on the deployment setup:
If we’re deploying ISE in a distributed deployment, we can have a maximum of two nodes with the PAN person enabled. One will act as a primary and the second as the secondary.
An ISE node with the monitoring persona enabled is used to centrally collect logs and generate user reports. Logs are sent via PAN (Policy Administration Node) and PSN (Policy Service Node) devices to the MnT node.
The node is then used for in-depth monitoring and troubleshooting of the entire network.
Logs are stored for each action that takes place within our network. As such, it’s important that the node running the MnT persona has enough storage for the retention required.
The MnT persona can be deployed using the following methods, depending on the deployment design:
As a minimum, at least one node within our deployment needs to be running the MnT persona. It’s also not recommended to run the MnT and PSN personas on the same node.
An ISE node with the policy service persona enabled acts as the RADIUS entry point for the network.
It’s used to provide the following services to the network:
The policy service node (PSN) evaluates policies configured within ISE and then makes the required decisions. An example being, is the device connecting allowed access to the network?
A number of nodes running the policy service persona can be deployed, depending on the size of the deployment. These nodes can then be used to spread the load of network requests into ISE. We’ll touch more on this on our upcoming lesson on Cisco ISE design.
The final persona that’s available is pxGrid. This persona is used to shared contextual information between external systems and ISE.
Some of the external systems that can be integrated with
Information can be shared unidirectionally or bidirectionally with pxGrid using inbuilt APIs.
A great example is the DNA-C appliance. This will hook into Cisco ISE via the pxGrid API. The DNA-C appliance then has the ability to read and gather contextual information regarding users on the network. It then has the ability to make changes to ISE. e.g. SGTs (Security Group Tags).
You can use Cisco pxGrid to share the context-sensitive information from Cisco ISE session directory with other network systems such as ISE Eco system partner systems and other Cisco platforms. The pxGrid framework can also be used to exchange policy and configuration data between nodes like sharing tags and policy objects between Cisco ISE and third-party vendors, and for other information exchanges. Cisco pxGrid also allows third party systems to invoke adaptive network control actions.”
Cisco ISE as a powerful solution for modern enterprises seeking robust identity management and network security. As organizations strive to secure their networks and streamline access control, the combination of Cisco's innovative ISE platform and the reliable support from Ctelecoms positions businesses for success. Embrace the future of network security with confidence, backed by the seamless integration of Cisco ISE and the expertise of Ctelecoms.