

2022/01/04 Cloud Backup & Disaster Recovery Solutions 1729 visit(s)
Cetelecoms
When talking about Microsoft Azure, we’re entering a whole new world of cloud capabilities, making creating and deploying applications and services an easy task like the 1,2,3.
And when we dive into this world we have to make a stop at the DevOps and DevSecOps to explore the features that every developer and enterprise in the tech industry needs.
So what are DevOps and DevSecOps? That’s what we’ll find out together in the next few lines.
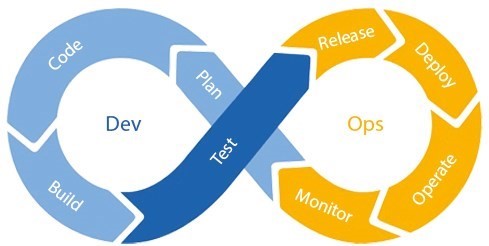
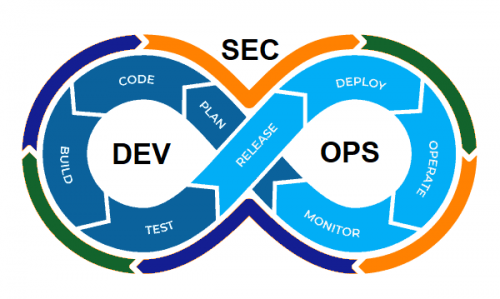
By definition, DevOps is an abbreviation for two words, Dev for development and Ops for Operations. In essence, it’s about the cooperation between software development and operation management; meaning between the developers and the operational team.
As for DevSecOps, the abbreviation gets security dragged into the middle and by definition, DevSecOps is the practice of building security into every phase of the software development lifecycle, including infrastructure.
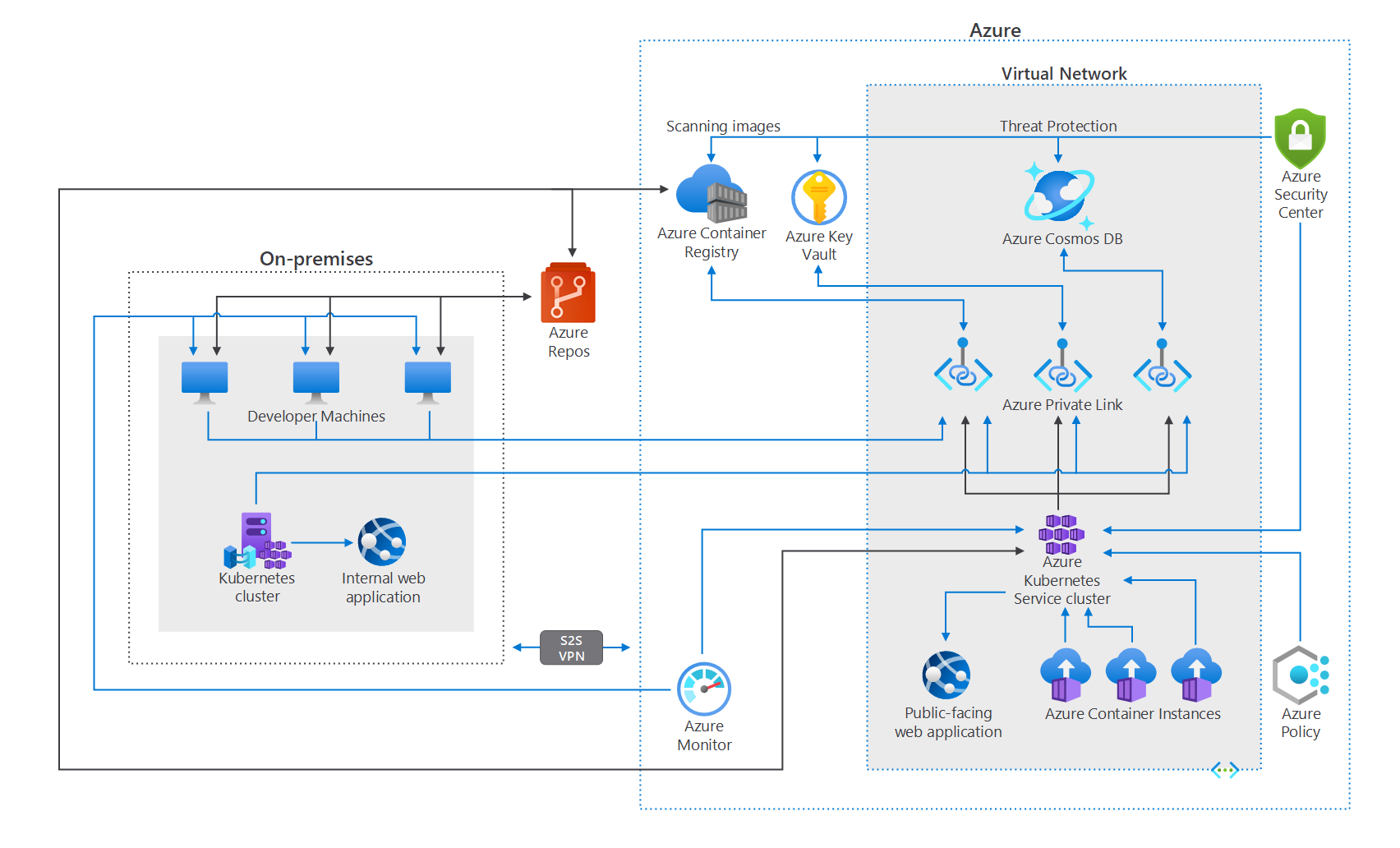
Now for Azure, there are a few best practices to help you secure your cloud infrastructure; including securing the perimeter, utilizing gold-hardened images from the Azure marketplace, managing server drift via containers and using immutable servers.
Read more: Cybersecurity Terminology: 30 Terms You Must Know!
Dive into Azure Virtual Networking
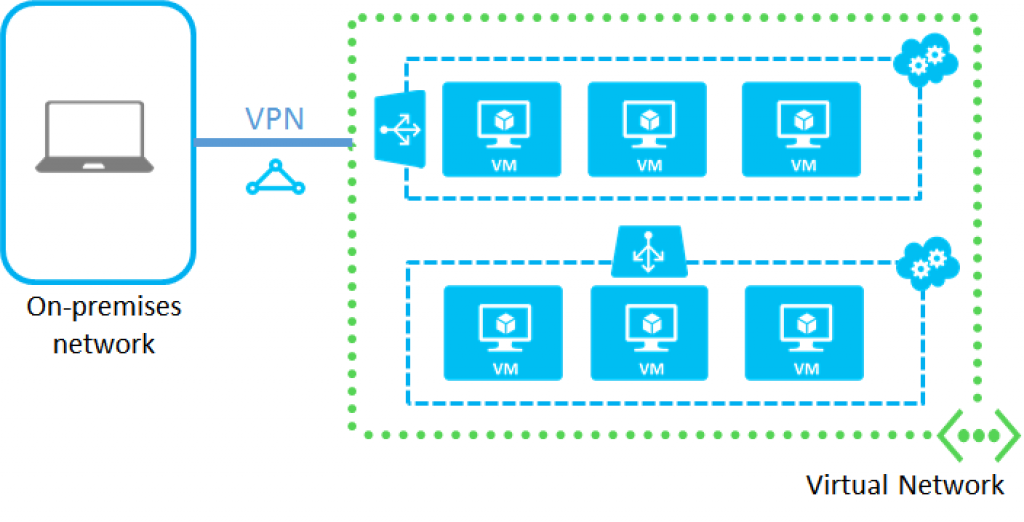
Here you can have full control over your network, from filtering network traffic to restricting access to network resources and routing the network traffic. All the previously mentioned practices can be done internally between your network infrastructure in the cloud as well as along the network’s perimeters.
Here you have to set up the right configurations to make sure you can take full advantage, like connecting devices to the same network, to the on-premises environment or even between virtual networks.
However, note that the wrong configuration can increase your network’s footprint and leave you open to cyberattacks.
The above-mentioned problem can be handled with the Zero Trust architecture.
Zero Trust differs from the traditional “perimeter security” model, where a weakness in the model can cause you many problems! The attacker in the model needs only to compromise one endpoint in order to access the entire network.
With Zero Trust, the issue is handled by removing implied trust across the entire network. The structure allows you to create multiple gates between your infrastructure’s endpoints in order to request trust validation at the time of access.
When talking about security measures in networks and clouds it’s really important to highlight the idea that you need to move the traffic in a way you can see and control. Therefore, with DevSecOps on Azure, you can control the traffic with user-defined routes.
When implementing user-defined routes, you can override the Azure defaults and specify where traffic is moving.
This practice will help you reduce network footprint and ensure that the right traffic is going to the right place, which in turn minimizes potential impact in case of a breach.
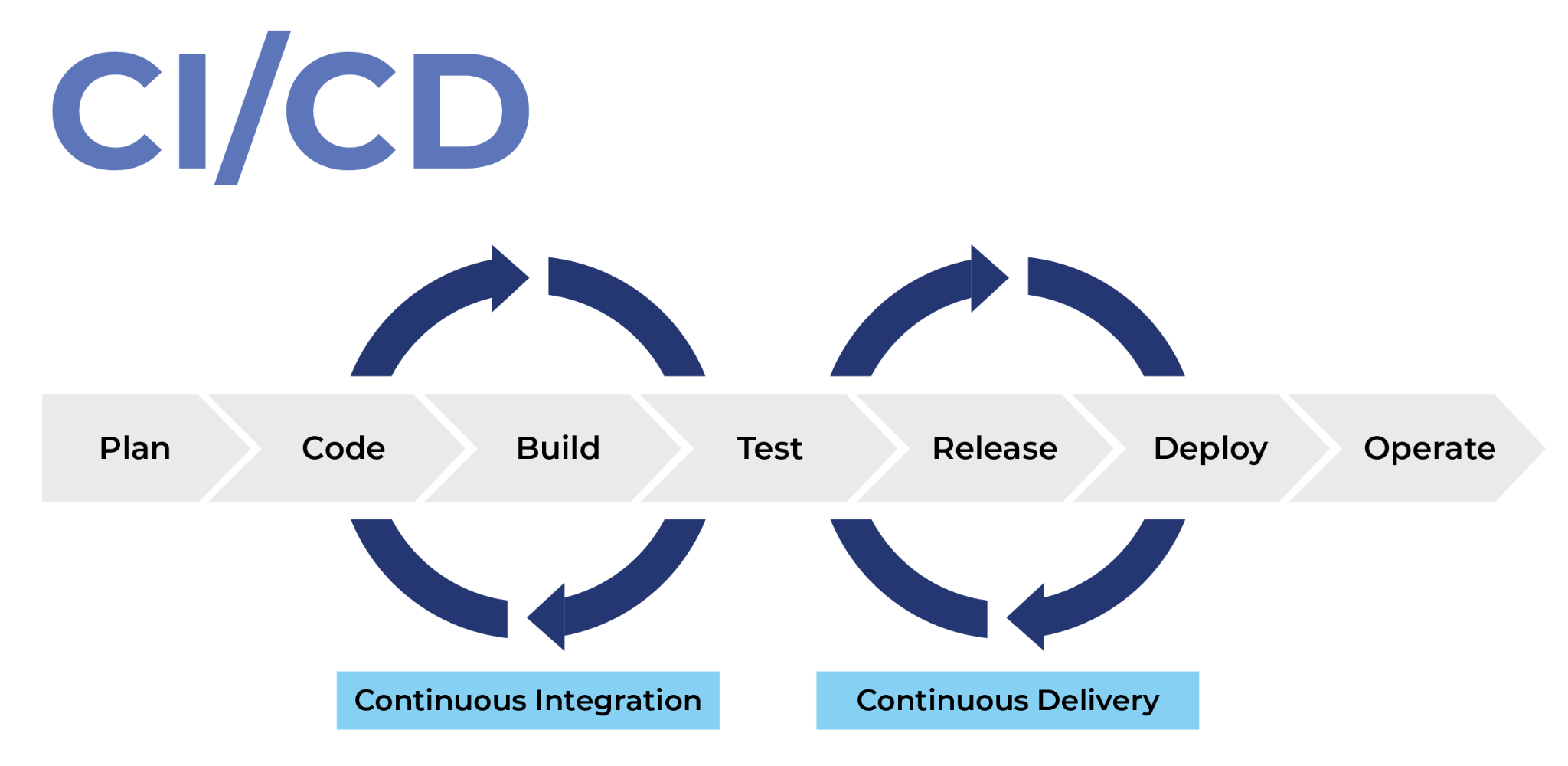
To begin with, CI/CD stands for “continuous integration” and “continuous delivery”, and in software engineering, we can agree that the CI/CD pipelines are getting more popular by the second. And in the following segment, we’ll explain the most common way to start with a solid foundation as you create your pipeline.
Hardened images or hardened virtual server images, is this virtual image devoid of everything unnecessary to the specific task at hand.
In a nutshell, hardened images allow you to deploy a securely configured virtual images of many different popular operating systems with pre-configured security settings attached.
How to create a gold-hardened image? You can take a hardened image, apply internal security requirements, install the necessary software, then apply the desired configuration and basically you’re good to go!
Whether you want to use a pre-hardened image or create your own, you’ll want to make sure you have implemented the following controls:
We know this can get really confusing at some point, but Microsoft made sure to explain it all through the documentation which you can view here.
There are lots of ways to secure your applications across platforms, however, here we’ll be focusing on two methods: Containerization and Immutability.
At first, let’s put it into simple words: A container is a standard package of software that bundles an application’s code together with the related configuration files and libraries and with the dependencies required for the app to run.
The first step to secure the Azure containers that you have is to use private repositories. The problem with public containers, like Docker Hub, for instance, don’t really guarantee security because each container has multiple layers of software and each layer might have vulnerabilities.
That’s why we strongly recommend creating and maintaining your own container registry since this is the only way to make sure that you are using correctly secured containers. However, if you were left with one option and that is using public containers, you can turn to using a private one such as Docker Trusted Repository or Azure Container Registry.
Simply because these registers are managed by the vendor, which in turn helps reduce vulnerabilities and attack threats.
With the help of Azure DevSecOps, you can recreate an environment when you get configurations changes simply by modifying the infrastructure code, which means that there is no need to implement new configurations on each server.
Immutability means that you are destroying the previous infrastructure, creating a new one, then deploying it.
Why the trouble? To eliminate the possibility of what we call “configuration drift” and keep your infrastructure as secure as possible.
Read more: The Benefits Of Using Microsoft Azure DevOps Services
Security measures must be your top priority when dealing with data and servers and trying to immune them along with your applications and networks, so why not turn to adopt DevSecOps as a solution? If you think that you might need help in this matter, contact Ctelecoms team, and our qualified specialists will guide you through the process. Let us support you at: https://www.ctelecoms.com.sa/en/Form15/Contact-Us