

2021/10/10 Microsoft Cloud Solutions 3464 visit(s)
Ctelecoms

Hello folks!
Today's blog offers real-life scenarios to help you learn how to use client access rules to allow or block different types of connections to Exchange.
What are clients in Exchange?
What are Client Access Rules?
What are client access components and properties (conditions)?
Learn how to use client access rules to allow or block different types of connection to exchange
The following are real scenario
Real Case scenario
Testing scenarios
All PowerShell commands
Reference links
As Microsoft says it applies to: Exchange 2013, 2016, 2019 and Exchange Online
Example Scenarios:
Desktop programs like outlook, Outlook on the web OWA, mobile clients (iPhone, android and others)
That are used to connect to exchange.
Clients and mobile in Exchange Online | Microsoft Docs
Controlling access to exchange online or as stated in Microsoft (exchange 2016 and 2019)
Based on client properties like transport rules.
The rules will have components is like conditional access policy in azure
Condition: Identify the client connections to apply the action to. Client Access Rules in Exchange Online | Microsoft Docs
Exceptions: Optionally identify the client connections that the action shouldn't apply to.
Action: Specifies what to do to client connections that match the conditions. (Allow or Block)
Priority: Indicates the order that the rules are applied to client connections (a lower number indicates a higher priority).
Now we need to control access for the clients
Block connection to exchange from specific IP range and allow users in IST department to bypass the rule.
This can be done by client access rules using PowerShell
Just go to internet type new-clientaccessrules you will have 2 links one for the procedures and the other is for syntax.
Procedures for Client Access Rules in Exchange Online | Microsoft Docs
New-ClientAccessRule (ExchangePowerShell) | Microsoft Docs
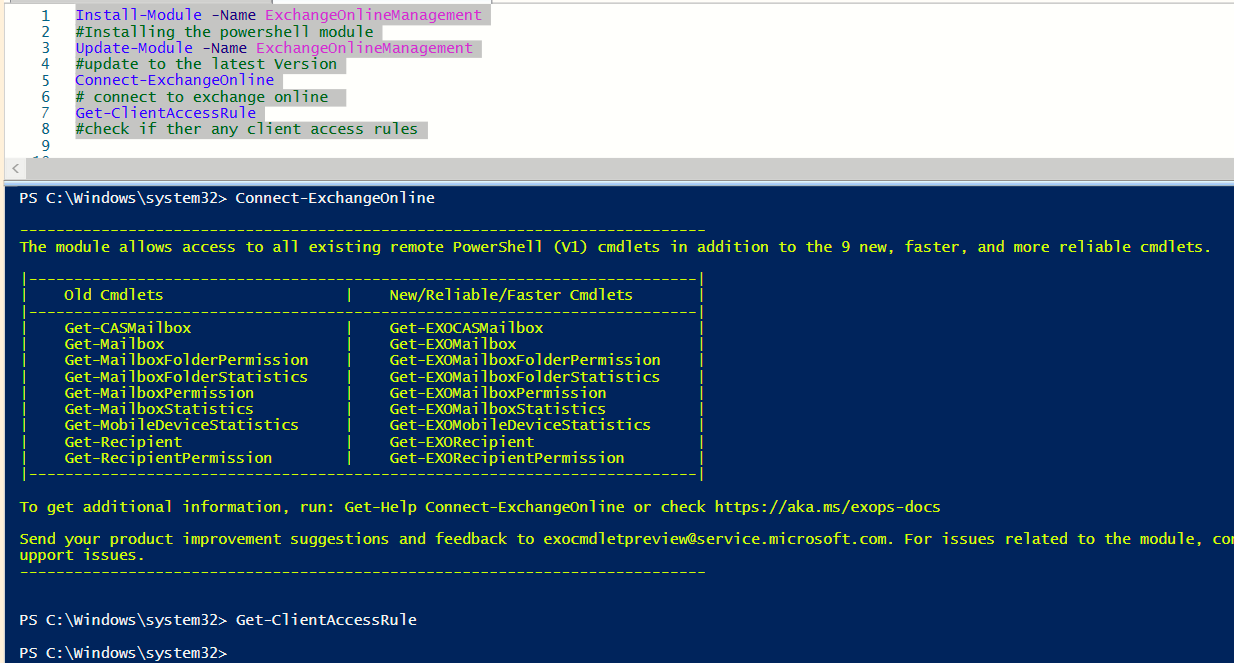
Run the following PowerShell commands to connect to exchange online
Install-Module -Name ExchangeOnlineManagement
#Installing the PowerShell module
Update-Module -Name ExchangeOnlineManagement
#update to the latest Version
Connect-ExchangeOnline
# connect to exchange online
Get-ClientAccessRule
#check if there are any client access rules
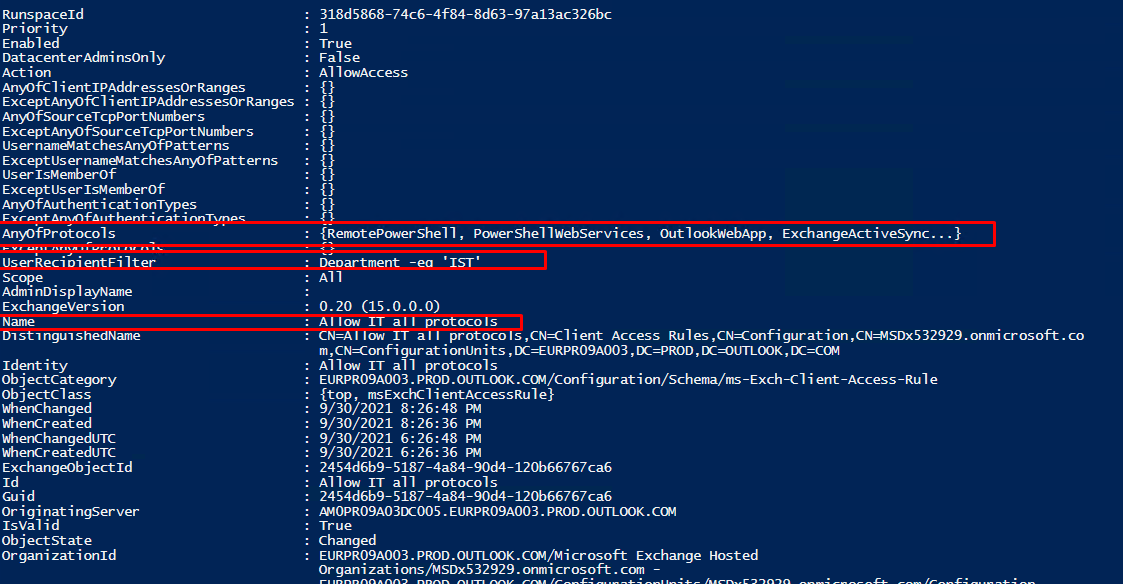
First rule scenario
Create a rule to block OWA outside of my company IP range
Then exclude IT Department from this rule
Notes: always crate the first rule to preserve the admin from this rule
Conditions, Exceptions, Action, Priority
New-ClientAccessRule -Name "
The following rule will have the first priority to exclude IST department from any rules
New-ClientAccessRule -Name "Allow IT all protocols" -Action Allow -AnyOfProtocols RemotePowerShell, PowerShellWebServices, OutlookWebApp, ExchangeActiveSync, ExchangeAdminCenter, ExchangeWebServices -UserRecipientFilter "department -eq 'IST'" -Priority 1
#Allowing it admins to bypass any rules (a lower number indicates a higher priority).
The highest priority you can set on a rule is 1
Procedures for Client Access Rules in Exchange Online | Microsoft Docs
![]()
Then check the components of the rule
Create a rule to block OWA outside of my company IP range you can also exclude a specific user
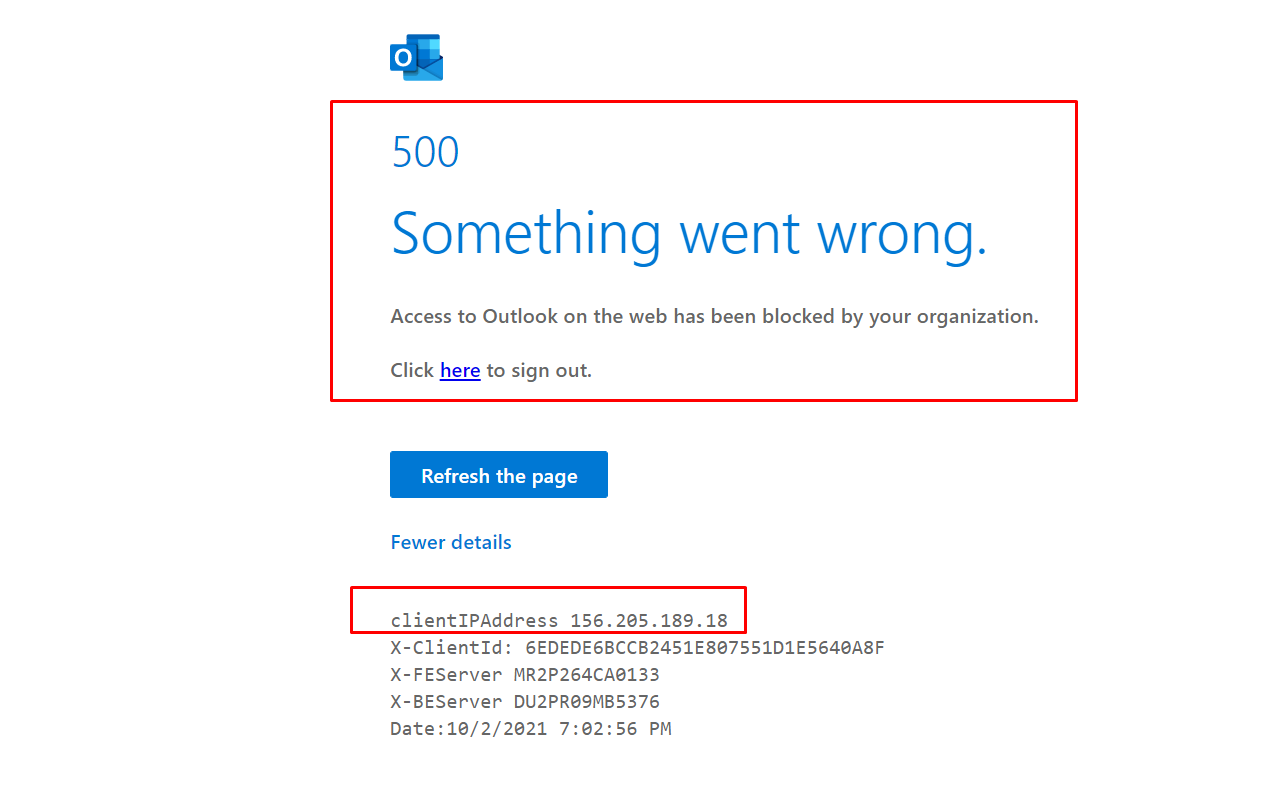
new-ClientAccessRule -Name "Block OWA from IP range" -Action DenyAccess -AnyOfProtocols OutlookWebApp -AnyOfClientIPAddressesOrRanges 156.205.189.18/30 - -Priority 2
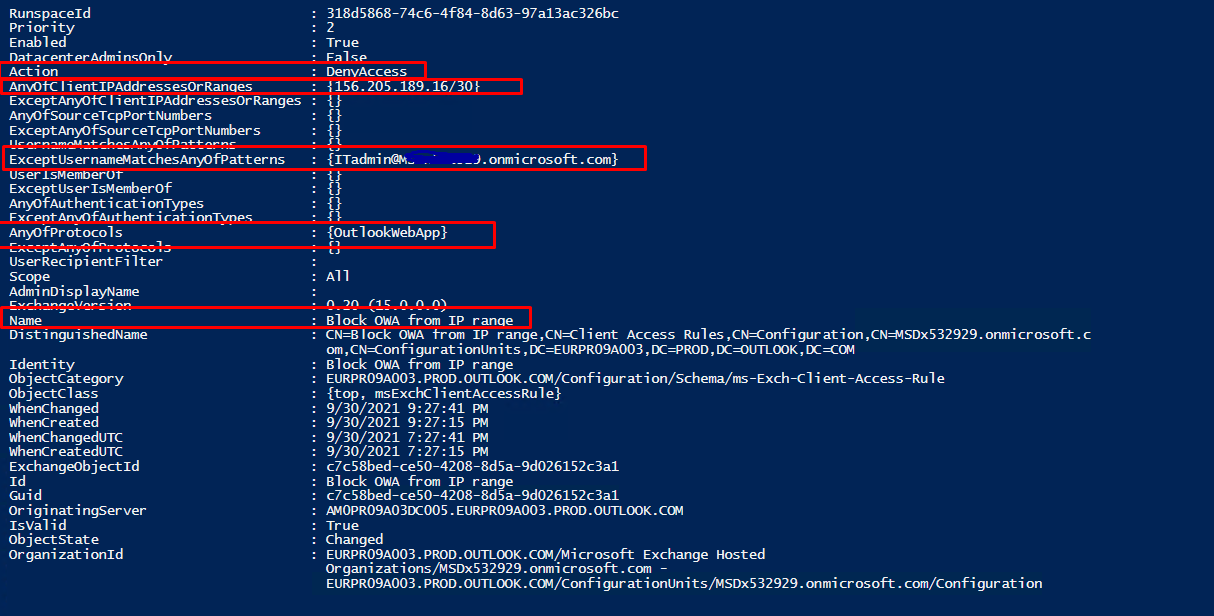
Get-ClientAccessRule -Identity "Block OWA from IP range" | FL
I shall have 2 rules now
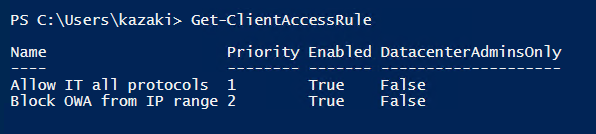
Now test using PowerShell command testing the it admin user
Note: The rules may need 24 hours for being applied then any other rules will take one hour
The first rule will be applied only so he bypasses the second rule
When we test using another IP rage not in the blocked list it is allowed, and rule has been applied which is allow
Test-ClientAccessRule -User username@yourdomain.com -Protocol OutlookWebApp -AuthenticationType BasicAuthentication -RemoteAddress yourIPblockedrange -RemotePort 443
Test-ClientAccessRule -User username@yourdomain.com -Protocol OutlookWebApp -AuthenticationType BasicAuthentication -RemoteAddress youripallowed -RemotePort 443
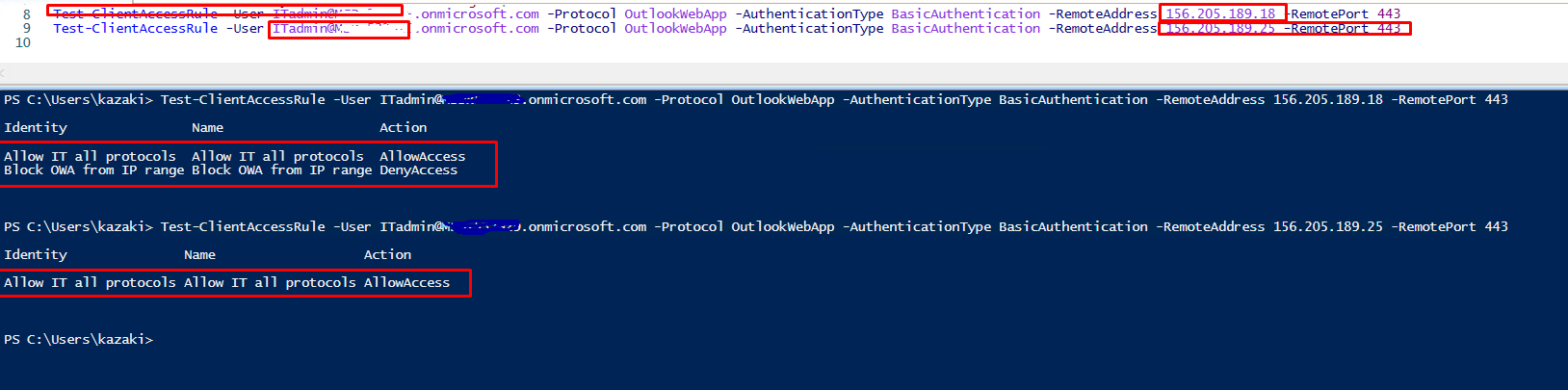
Testing another user not in IST department
The rule was applied when accessing from blocked IP range
Then when in another range no rule applies
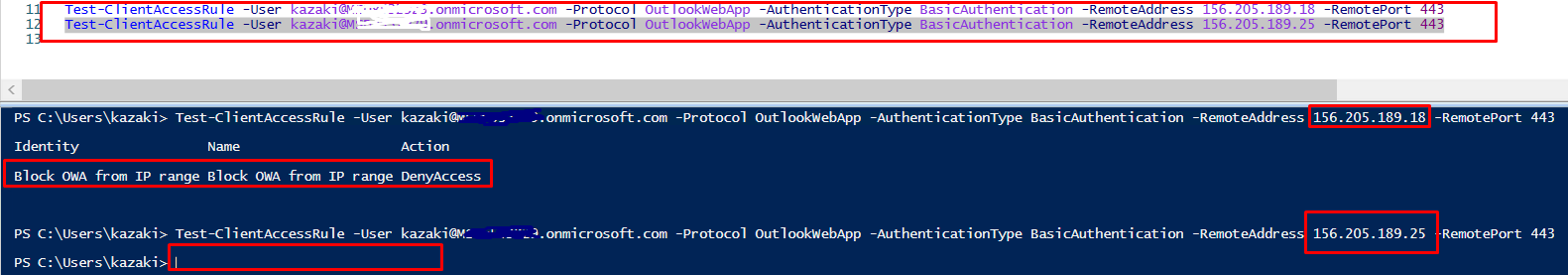
Now testing the log in for IT Admin account from range blocked and not blocked he can access
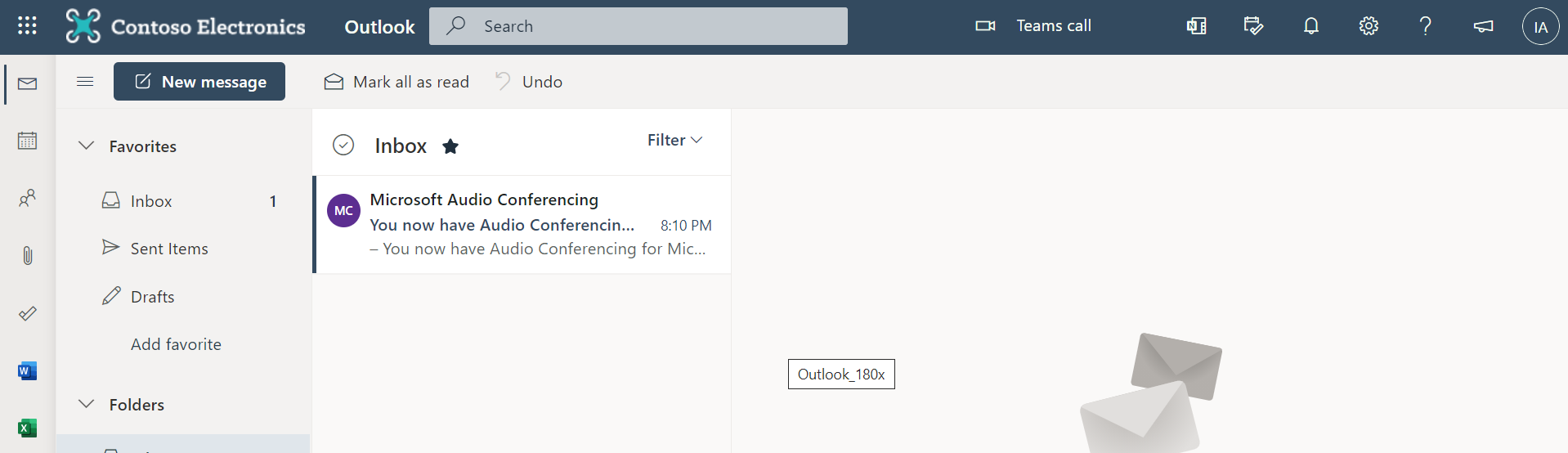
Let’s test with another user isn't in the exception
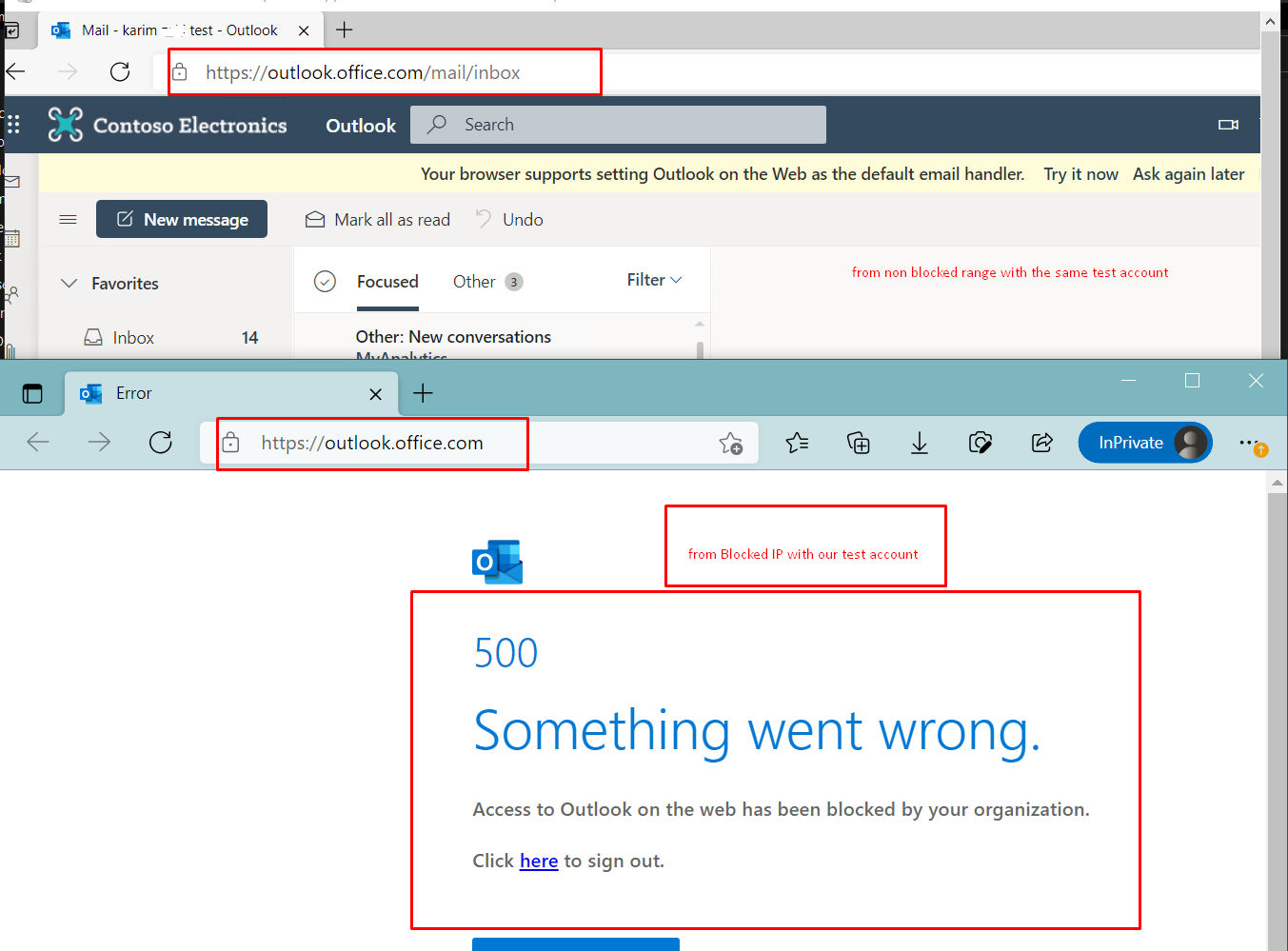
Now I will test with account it admin excluded from this rule
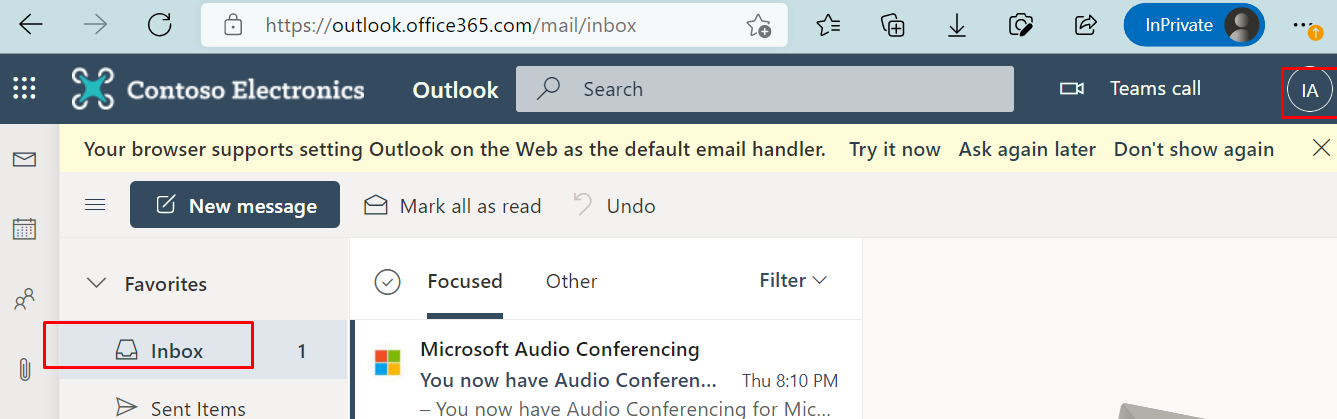
Please replace the following (it admin, blocked user, allowed Ip, blocked Ip ) with your real data
Install-Module -Name ExchangeOnlineManagement
Connect-ExchangeOnline
New-ClientAccessRule -Name "Allow IT all protocols" -Action Allow -AnyOfProtocols RemotePowerShell, PowerShellWebServices, OutlookWebApp, ExchangeActiveSync, ExchangeAdminCenter, ExchangeWebServices -UserRecipientFilter "department -eq 'IST'" -Priority 1
new-ClientAccessRule -Name "Block OWA from IP range" -Action DenyAccess -AnyOfProtocols OutlookWebApp -AnyOfClientIPAddressesOrRanges Blockedrange - -Priority 2
Get-ClientAccessRule
Get-ClientAccessRule -Identity "Allow IT all protocols" | FL
Get-ClientAccessRule -Identity "Block OWA from IP range" | FL
Test-ClientAccessRule -User ITadmin@yourdomain.com -Protocol OutlookWebApp -AuthenticationType BasicAuthentication -RemoteAddress BlockedIP -RemotePort 443
Test-ClientAccessRule -User ITadmin@yourdomain.com -Protocol OutlookWebApp -AuthenticationType BasicAuthentication -RemoteAddress AllowedIP -RemotePort 443
Test-ClientAccessRule -User blockeduser@domain.com -Protocol OutlookWebApp -AuthenticationType BasicAuthentication -RemoteAddress BlockedIP -RemotePort 443
Test-ClientAccessRule -User blockeduser@domain.com -Protocol OutlookWebApp -AuthenticationType BasicAuthentication -RemoteAddress AllowedIP -RemotePort 443
Reference links:
New-ClientAccessRule (ExchangePowerShell) | Microsoft Docs
Client Access Rules in Exchange Online | Microsoft Docs
Procedures for Client Access Rules in Exchange Online | Microsoft Docs