

2023/05/07 Microsoft Cloud Solutions 1855 visit(s) 4 min to read
Ctelecoms
We are thrilled to announce the latest enhancements and upgraded capabilities for Microsoft Defender Vulnerability Management. As vulnerability management is a constantly evolving field, we believe that these updates will help you improve your vulnerability management program and provide better protection for your organization. Our April update introduces a range of new enhancements and capabilities, including the following:
* Improved security baseline assessments: including new Microsoft benchmarks, as well as the option to exclude specific configurations on certain devices from being assessed.
* The update introduces a new feature that provides information about the reboot status of devices, labeled as "Pending restart".
* Vulnerability management APIs now allow you to view data for devices that are not onboarded.
Microsoft Defender Vulnerability Management's security baseline assessment is an automated solution that enables customization of configuration checks and management of exceptions. It offers precise, up-to-date configuration values and evidence for various operating systems, along with recommended values from a broad range of benchmarks to assist SOC teams in achieving their mission of ensuring their organizations' safety.
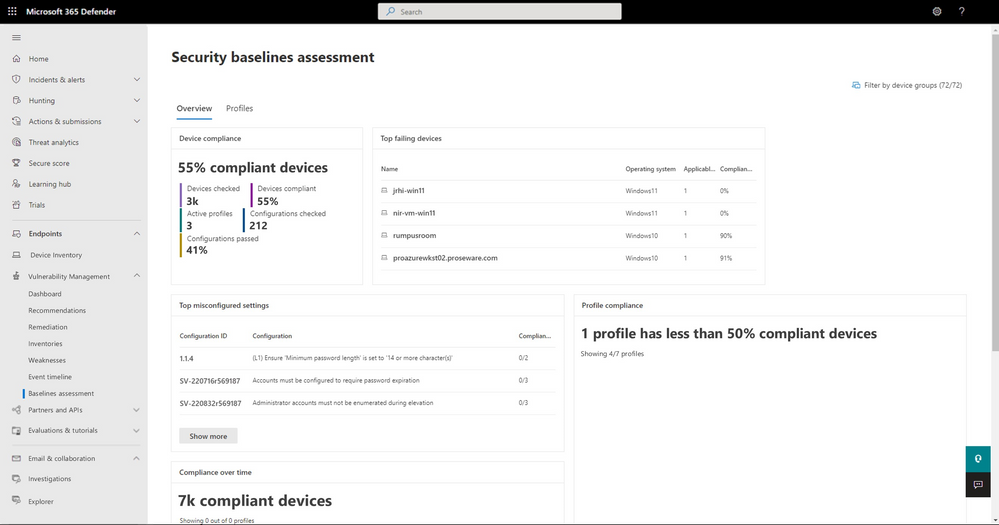
Figure 1: Monitor and track the status of your compliance with the security baseline assessment dashboard.
Rather than conducting endless compliance scans, the security baseline assessment feature enables organizations to monitor security baseline compliance continuously and seamlessly, identifying any changes in real-time. We are thrilled to announce a few updates that have been developed to improve this premium feature:
Our latest capability provides security teams with the ability to focus on critical systems and applications, while also exercising caution when utilizing exception management.
With the new exceptions’ capability in the security baseline assessment, it is now possible to exclude particular devices and configurations from the configuration check profiles. This ensures that these devices are no longer active in the profiles, which won't impact the organization's metrics and score. This capability enhances management and control abilities, as well as provides greater visibility into compliance. To learn more about this update, , read more about security baseline assessments here.
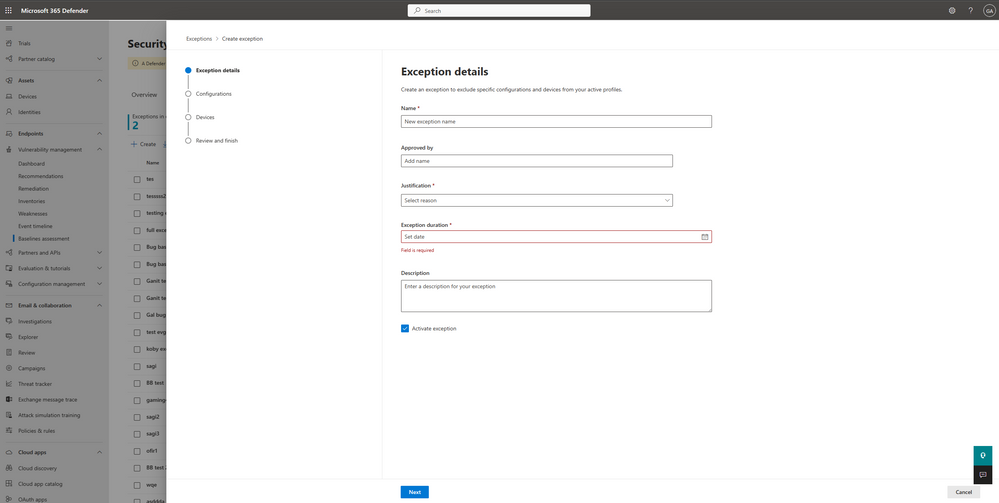
Figure 2: Define exception - enter details, choose the scope, and select the configurations and devices you want to exclude.
The existing collection of CIS and STIG benchmarks has assisted organizations in identifying recommended security settings and configurations that comply with regulatory and industry standards. In addition to these benchmarks, organizations can now utilize Microsoft benchmarks to optimize their Microsoft environments. Starting today, enterprises will have the ability to manage and assess configurations against the Microsoft benchmarks.
Patching process is a crucial aspect of a comprehensive vulnerability management solution. To assist organizations in monitoring their patching status, Microsoft has created a new capability that enables tracking of device status during the patching process. This capability will indicate whether the patching has failed due to a pending restart, and it will also provide the number of devices that are pending a restart.
The development of this new feature aims to address the gap that can arise between update actions taken and the exposure metrics that do not yet reflect these actions. This gap can occur in many cases because some devices require restarts to complete an update.
This indication can be found in multiple locations within Defender Vulnerability Management. A pending restart tag is now included in security recommendations, and on the software page, it appears as part of the missing KBs section. Currently, this new capability covers Windows (OS) updates and KB corrections as the first step. Microsoft plans to extend this feature to many other operating systems in the future.
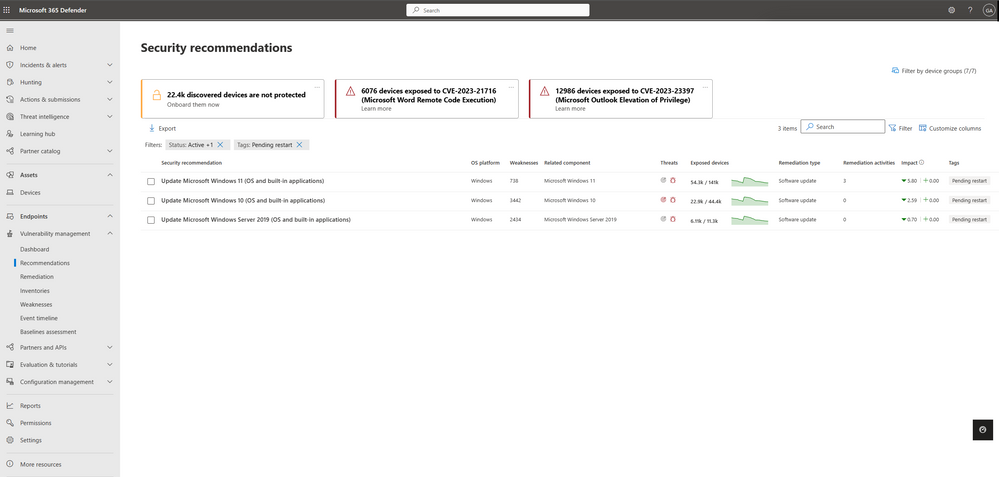
Figure 3: Review security recommendations associated with devices that are pending restart by filtering on the appropriate tag.
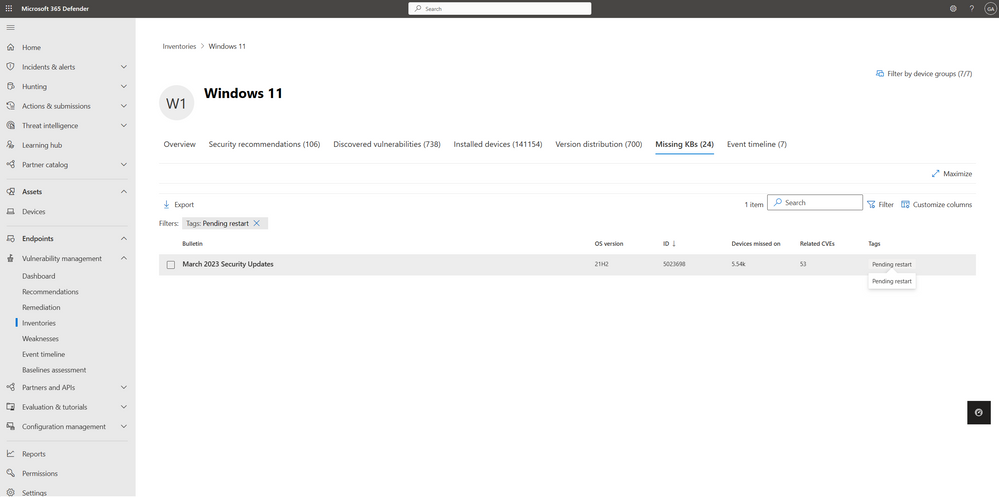
Figure 4: Review missing KBs associated with devices that are pending restart through the software page.
Customers have been utilizing Microsoft Defender Vulnerability Management APIs to generate customized reports and dashboards that offer valuable insights into their organization's security posture. Defender Vulnerability Management API has typically provided data for devices that have been onboarded to Microsoft Defender for Endpoint, as the vulnerability management export APIs retrieved data on a per-device basis. The file exports included only onboarded devices, and the 'IsOnboarded' field in the export was always set to 'True.'
In the following weeks, Microsoft will be implementing an update to the Defender Vulnerability Management API that will enable the retrieval of data on devices that have not been onboarded to Microsoft Defender for Endpoint. With this update, organizations will have access to more comprehensive information about their devices, allowing for the creation of more detailed reports to monitor devices and risks more effectively. This update will apply to vulnerability management API exports via files, and the export file will now include data on devices that have not been onboarded to Microsoft Defender for Endpoint.
As a result, the additional data may result in much larger export files for the vulnerability management APIs due to inclusion of both onboarded and not yet onboarded devices.
While there is no action needed to prepare for this change, it is important to note that the amount of data exported may be significantly larger. Therefore, to manage the data exported within your data export tools, it is recommended that you apply a filter to control the exported data's volume.
Ctelecoms, as a Gold Microsoft Partner, offers top-notch solutions to customers in Saudi Arabia. If you want to learn more about the preview, simply click on the link and contact us. Our team will be delighted to provide you with any assistance you need: https://www.ctelecoms.com.sa/en/Form15/Contact-Us