

2024/09/24 Microsoft Cloud Solutions 1984 visit(s) 4 min to read
Ctelecoms

Azure Sentinel, now known as Microsoft Sentinel, is a cloud-native security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution that runs in the Azure cloud. Microsoft Sentinel is designed to enable comprehensive security operations, offering a range of capabilities for data collection, detection, response, and investigation. It can be used for security event analysis in both cloud and on-premises environments. Common use cases include:
- Quick setup – Sentinel can be deployed via the Azure portal in a matter of minutes, eliminating the need for time-consuming server installation in the cloud or on-premises.
- Sentinel offers a comprehensive range of connection options, enabling users to ingest data through various methods, including Function Apps, Logic Apps, Agents, Syslog, and native codeless connectors.
- Automated threat response: Sentinel employs playbooks and deploys the capabilities of Azure Logic Apps to provide automated threat response capabilities.
Microsoft Sentinel is a centralized platform that streamlines your organization’s threat collection, detection, response and investigation efforts. It provides comprehensive threat intelligence and intelligent security analytics, enabling enhanced visibility, alert detection, threat response and proactive threat hunting.
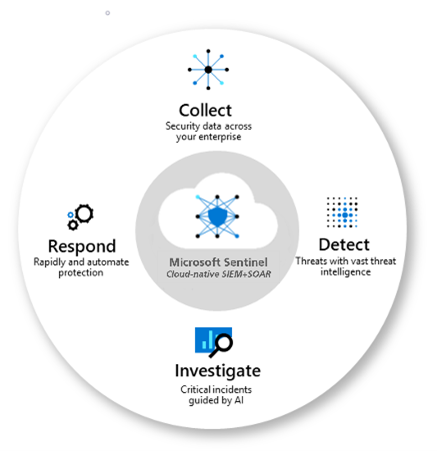
Microsoft Sentinel works according to a cycle that starts with log management, continues to schema normalization, data validation, detection and investigation, and includes automated responses to alerts. Here is how Sentinel delivers this end-to-end functionality:
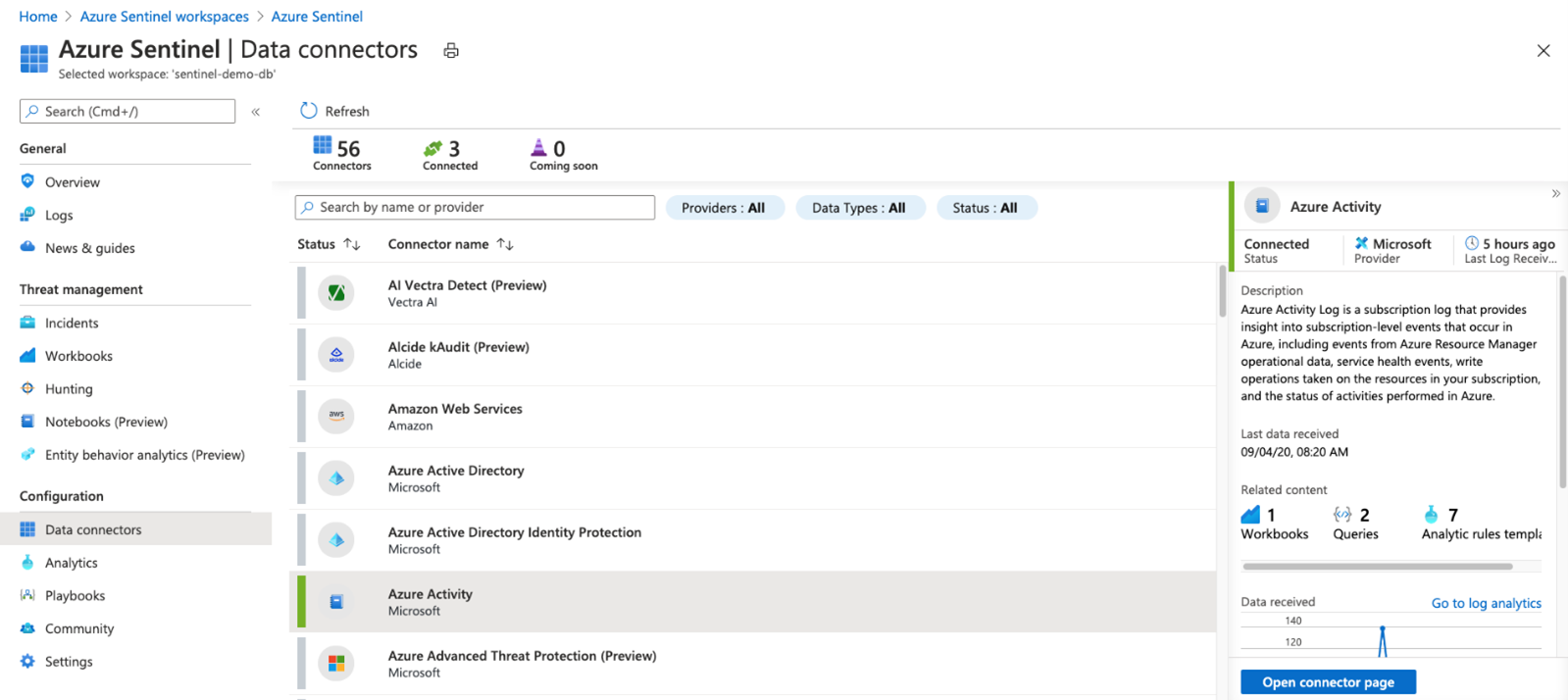
Data connectors allow Microsoft Sentinel to import data from a range of sources.
In certain cases, you can add a service, such as Azure activity logs, by clicking a button. Some services, such as syslog, may require configuration.
Sentinel offers data connectors for a range of common sources and scenarios, including syslog, cloud platforms such as Amazon Web Services (AWS) and Microsoft Azure, Common Event Format (CEF), and Trusted Automated eXchange of Indicator Information (TAXII). Additionally, custom applications, distinctive non-security logs, and physical security (OT) logs can be integrated into Microsoft Sentinel.
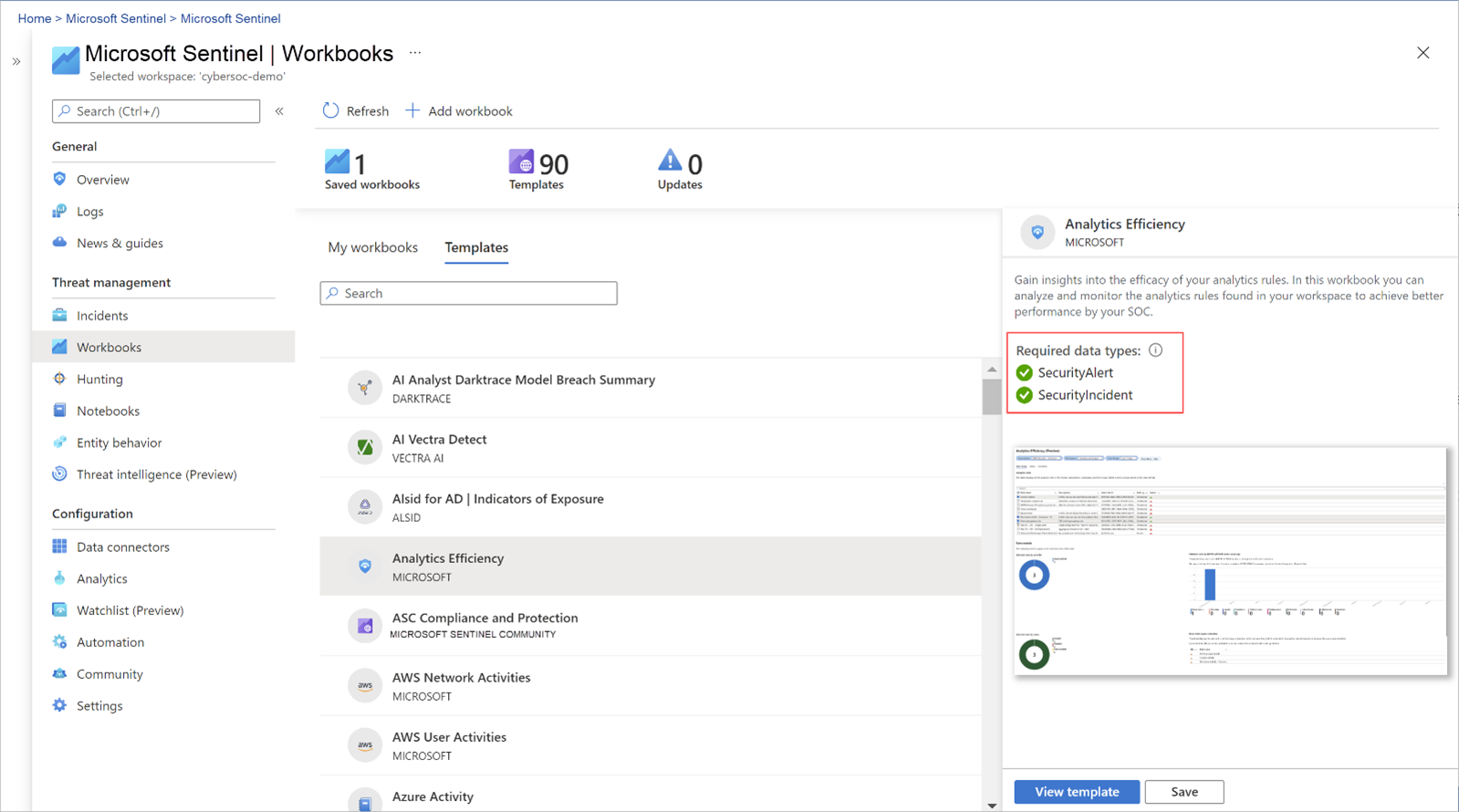
Sentinel allows users to integrate workbooks to monitor, measure, and control their data. A variety of templates are available to create custom and interactive workbooks, which can be viewed in Sentinel. Built-in Sentinel workbook templates can be used to gain insights immediately after connecting a data source. Custom workbooks can be created to assist with investigation workflows, executive reporting, or to monitor for specific anomalies with WAF, for example.
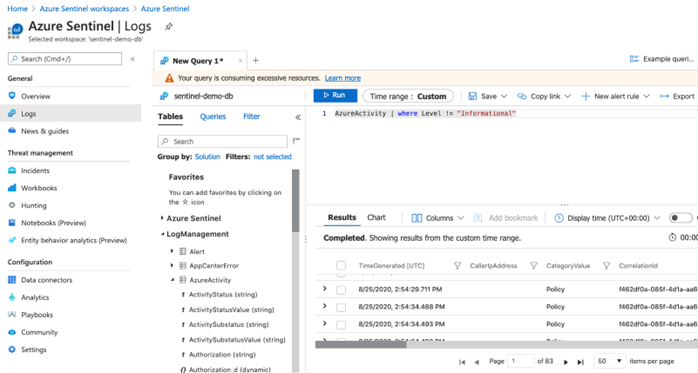
Sentinel stores imported data using Log Workspaces. Additionally, logs can be forwarded for long-term storage to ADX. Querying in Microsoft Sentinel requires a knowledge of the Kusto Query Language (KQL). Please refer to this Microsoft tutorial on the basics of KQL for more information.
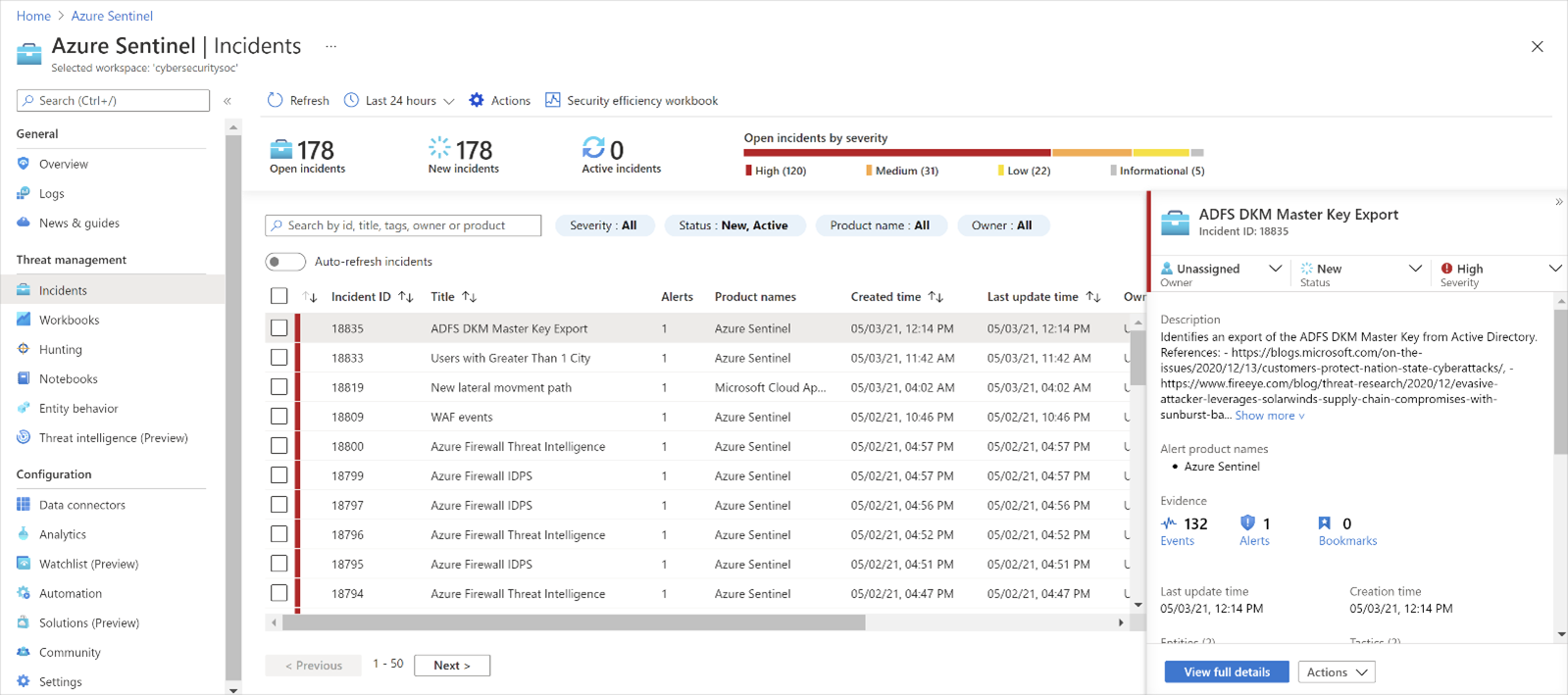
The purpose of analytic rules, or SIEM content, is to correlate alerts into incidents. Analytical rules can be scheduled queries or queries run on demand. An incident is a group of related alerts that, taken together, represent a potential threat. Grouping alerts into categories allows you to investigate and resolve multiple alerts simultaneously. Sentinel offers built-in correlation and machine learning rules to help map your network's behavior and detect anomalies. However, to obtain maximum value, these rules will require tuning within your environment. Some rules combine low-fidelity alerts from different entities into a potential high-fidelity security incident. Customizing rules, while requiring an initial investment, can save hours of investigation time on false positives.
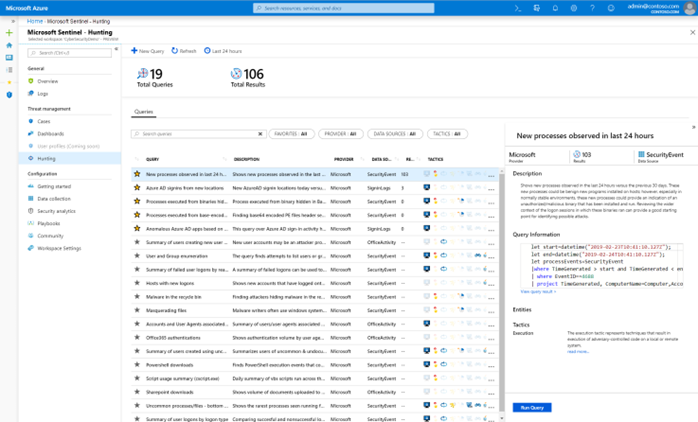
By forwarding Microsoft 365 logs to Sentinel, organizations can enhance their threat hunting beyond EDR capabilities. This process involves identifying threats that bypassed existing controls, using detection content from Microsoft or other intelligence. Security analysts adopt a zero trust, “assume breach” mindset to uncover sophisticated threats already in the environment.
Here is how you can use this feature:
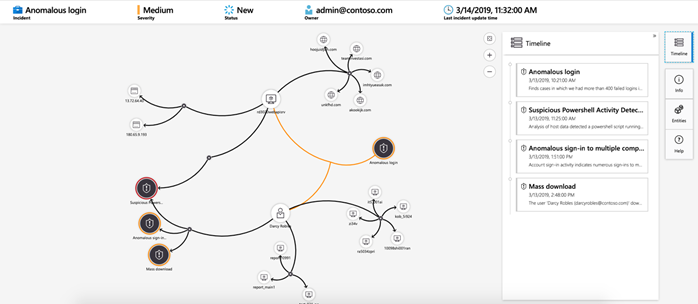
Sentinel creates an incident when an alert is triggered. Automation can also be tied to an incident firing. You can investigate these incidents using the following capabilities:
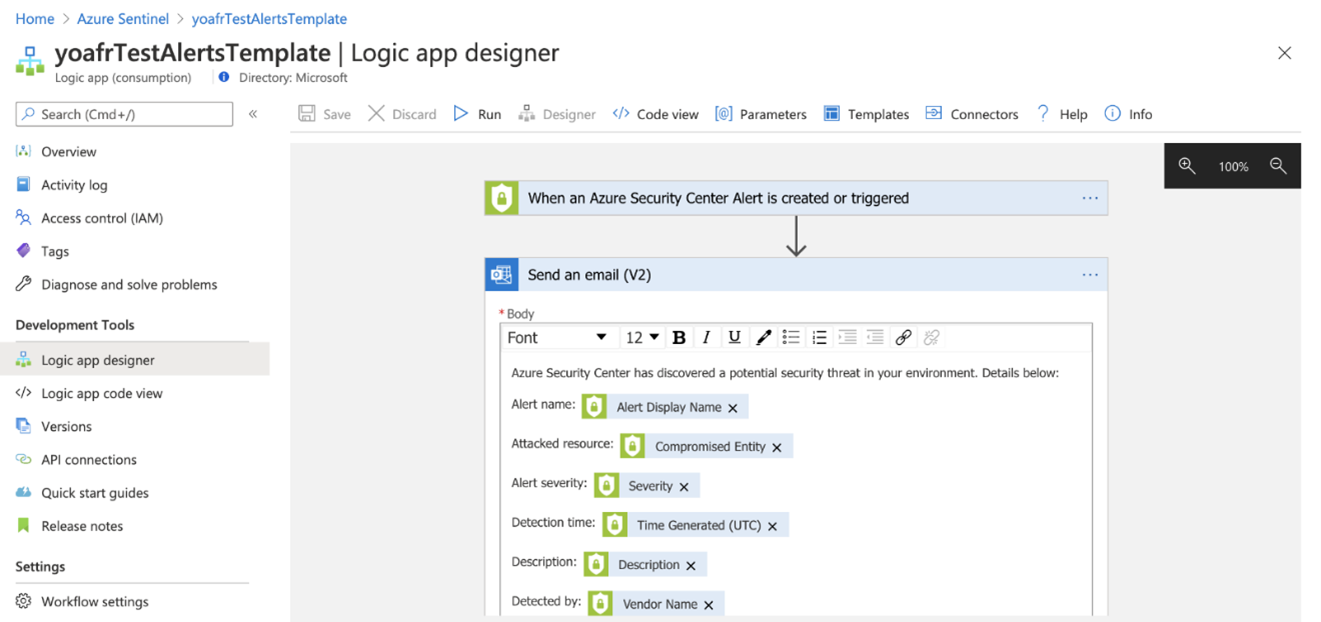
Sentinel offers SOAR capabilities that can assist with enrichment, containment, integration with an ITSM system, or other forms of automated incident response. By using Azure Logic Apps or Azure Functions, we can create automated playbooks to reduce analyst overhead, decrease response times, or integrate workflows between security and observability.
Microsoft Sentinel is a cloud-based solution, with fees based on the selected service tier and the amount of data captured for analysis and stored in the Azure Monitor Log Analytics workspace.
It is important to consider the cost of a log source in relation to its value in terms of both detection and investigation. It may also be advisable to temporarily enable a log source and disable it in cases where the log source is no longer relevant or the threat profile has changed. The most effective way to budget for SIEM costs is to implement a capacity plan.
Microsoft Sentinel offers two payment methods:
- The pay-as-you-go option allows customers to pay for the data they use, with charges applied per ingested GB. Furthermore, Azure may apply fees for data import to the Log Analytics service.
- Capacity Reservation: This option requires users to commit to a certain number of GB of storage per day, with a flat daily price for storage applied. This model offers savings of up to 65% compared to pay-as-you-go.
- The Microsoft 365 E5 licence provides a data grant of up to 5MB/user/day to ingest Microsoft 365 data.
- Certain Microsoft 365 data sources are free for Microsoft Sentinel users, including Azure Activity Logs, Office 365 Audit Logs, and Alerts from Microsoft Defender security products.
Ctelecoms, as a Microsoft Gold Partner in Saudi Arabia, is here to help local companies seamlessly adopt Microsoft solutions. We understand the unique needs of Saudi businesses and provide tailored support to ensure a smooth transition. Whether it’s enhancing productivity with Microsoft 365 or optimizing cloud services with Azure, we’re dedicated to empowering your organization with the right tools for success.
Let’s take your business to the next level together!