

2024/11/05 IT & Cyber-Security Solutions 1276 visit(s) 5 min to read
Ctelecoms

Zero Trust deployment plan with Microsoft 365 | Microsoft Learn
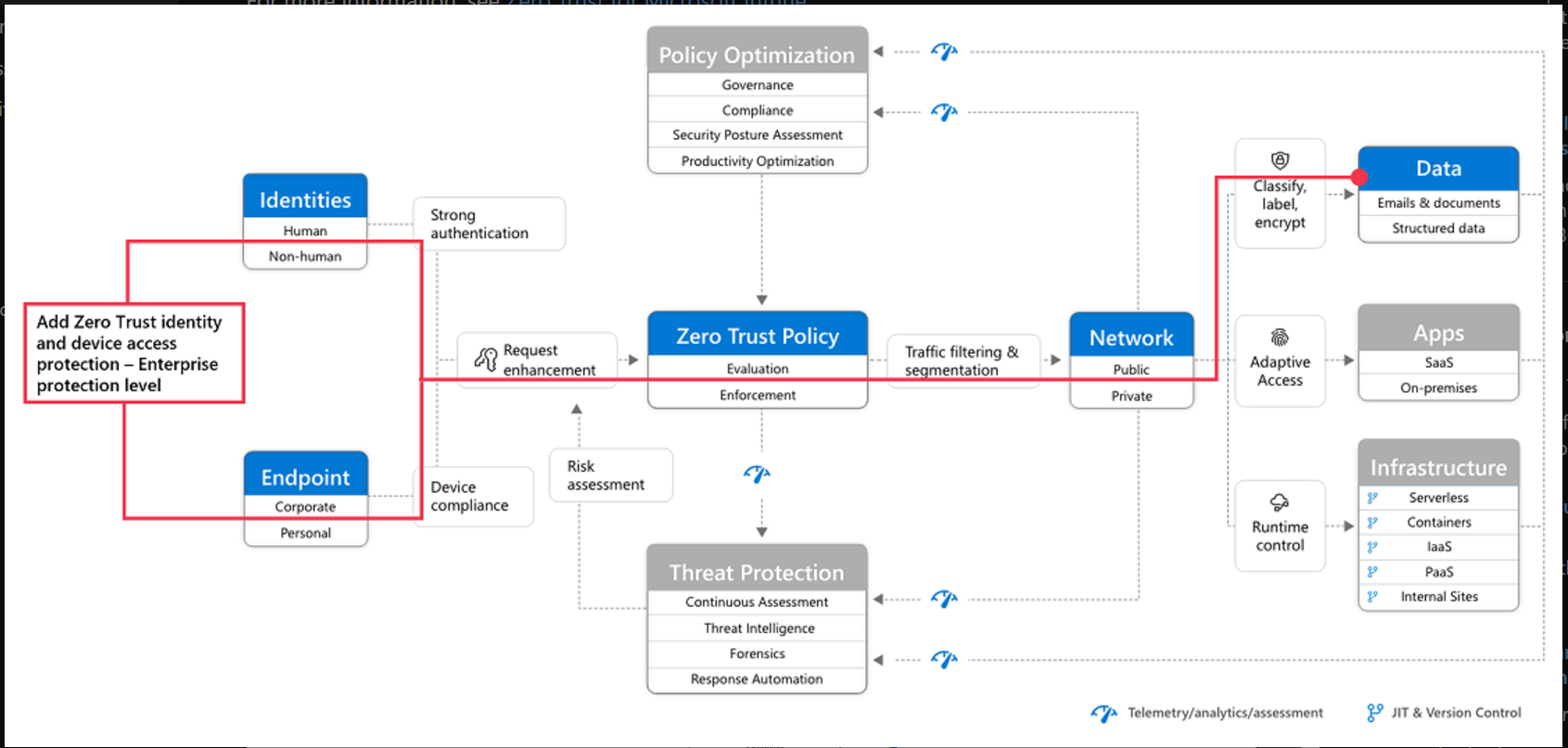
And also in Top 12 tasks for security teams to support working from home
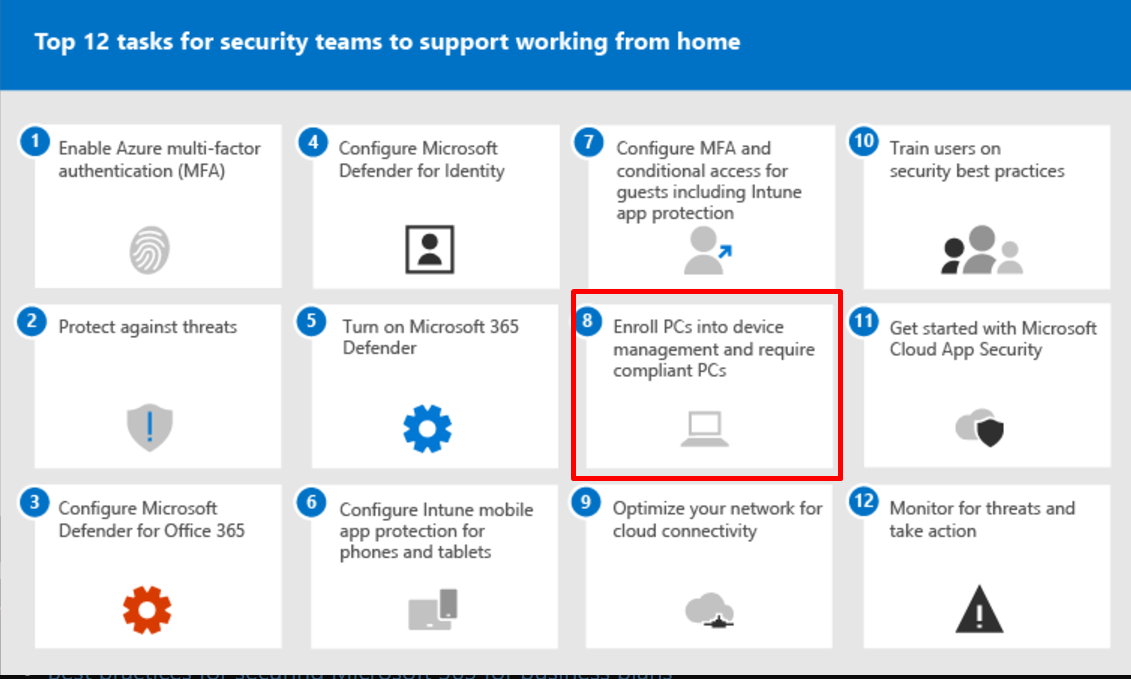
Top 12 tasks for security teams to support working from home | Microsoft Learn
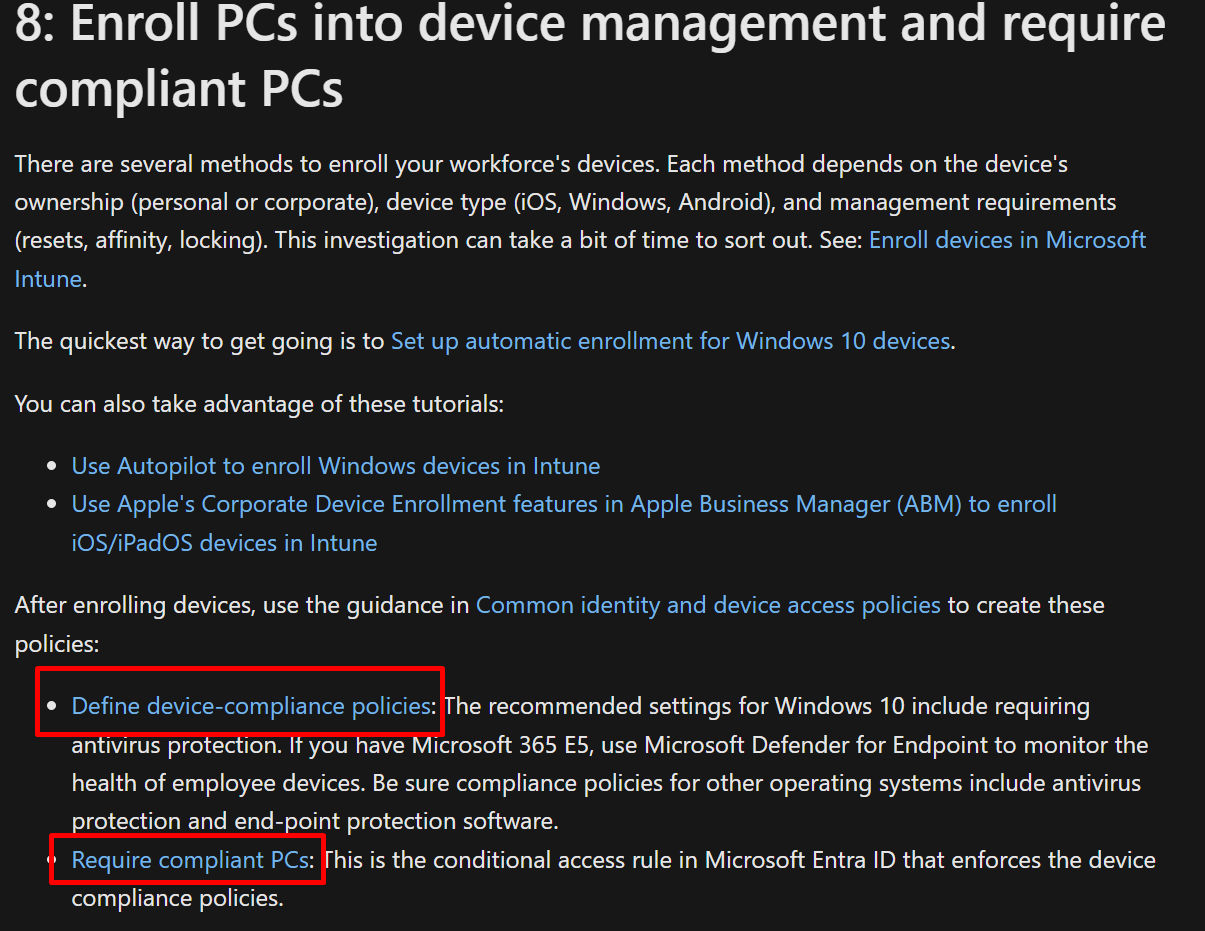
This is in the conditional access policy and it make the respect to be the to the policy in sharepoint.
So, when configure from sharepoint admin center it created these 2 policies you shall go and exclude the Global admin and your self, as bellow:
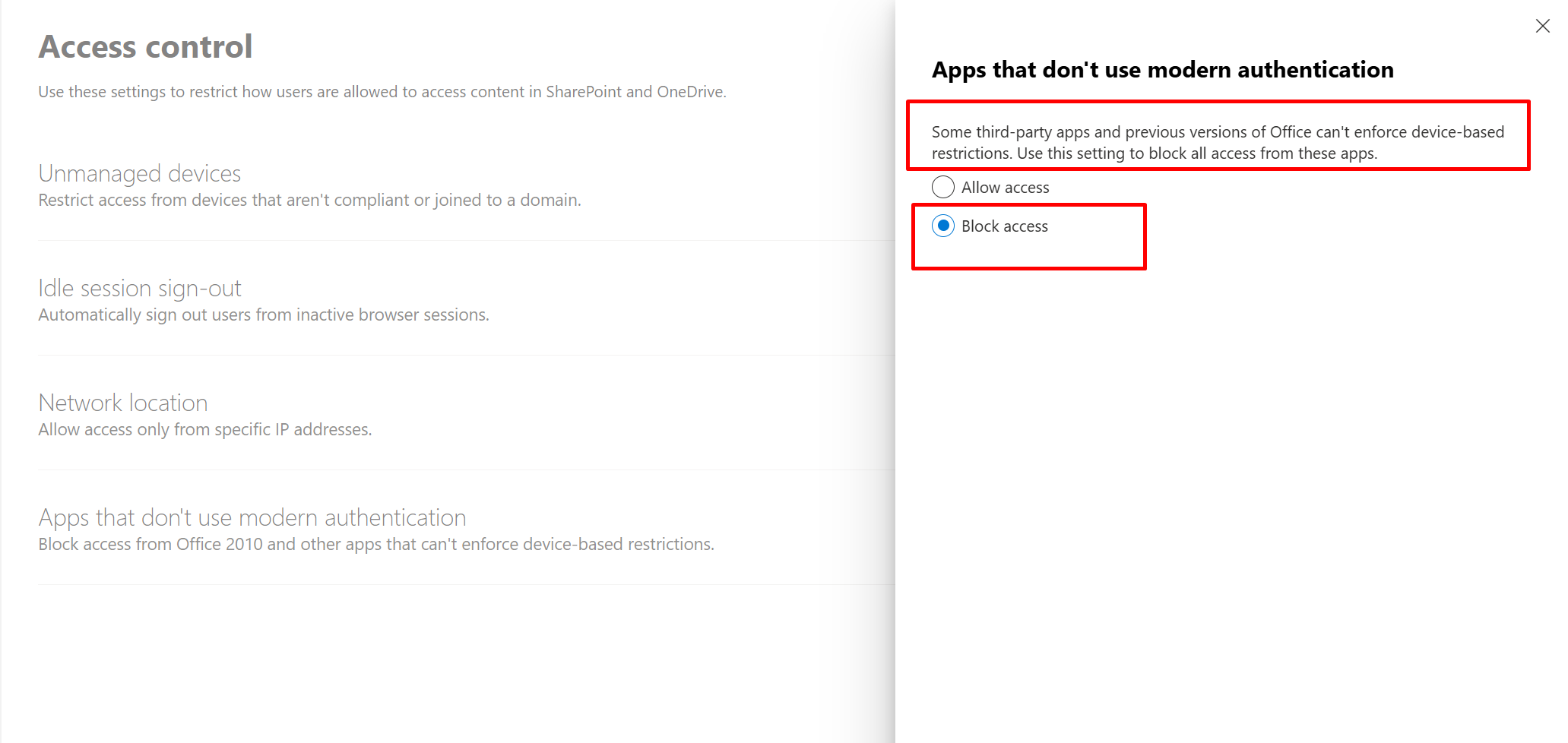
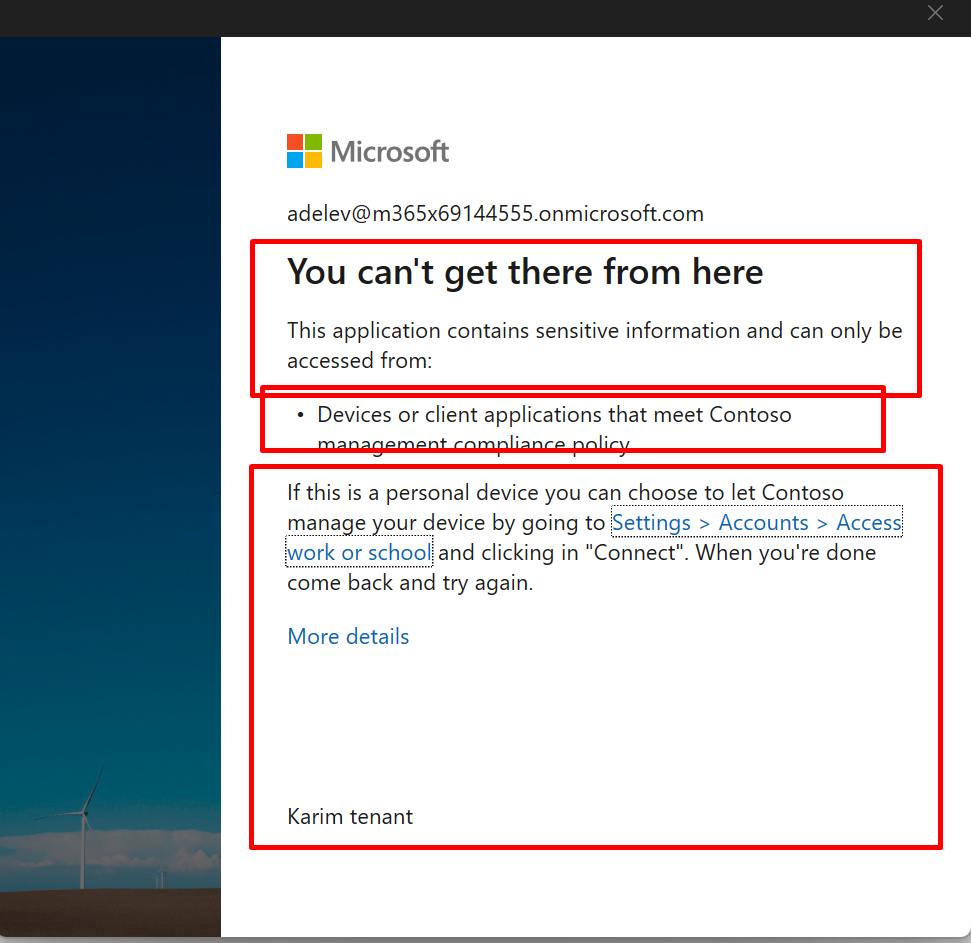
Organizations can use this control to require Microsoft Entra ID to pass device information to the selected cloud apps. The device information allows cloud apps to know if a connection is from a compliant or domain-joined device and update the session experience. When selected, the cloud app uses the device information to provide users with a limited or full experience. Limited when the device isn't managed or compliant and full when the device is managed and compliant.
For a list of supported applications and how to configure policies, see the following articles:
Idle session timeout for Microsoft 365 - Microsoft 365 admin | Microsoft Learn
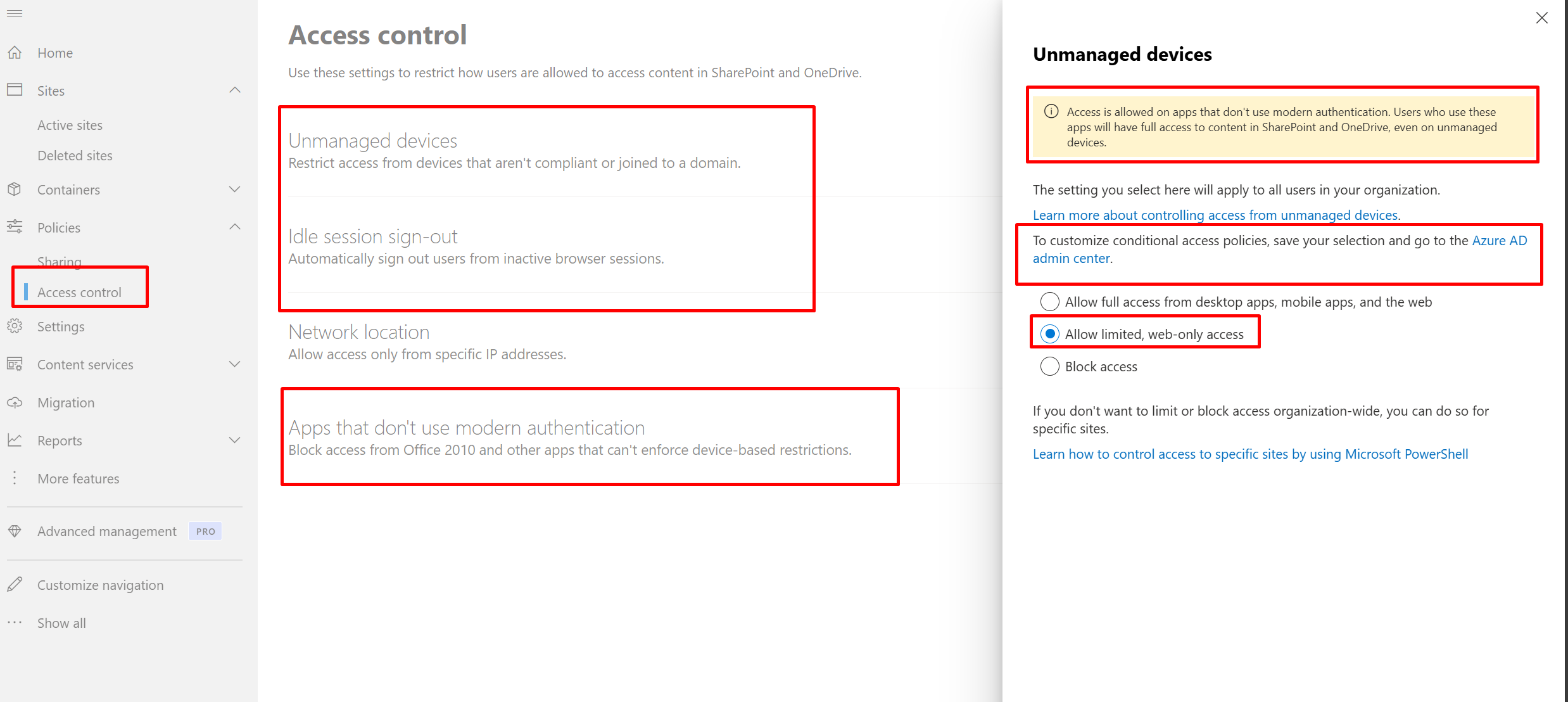
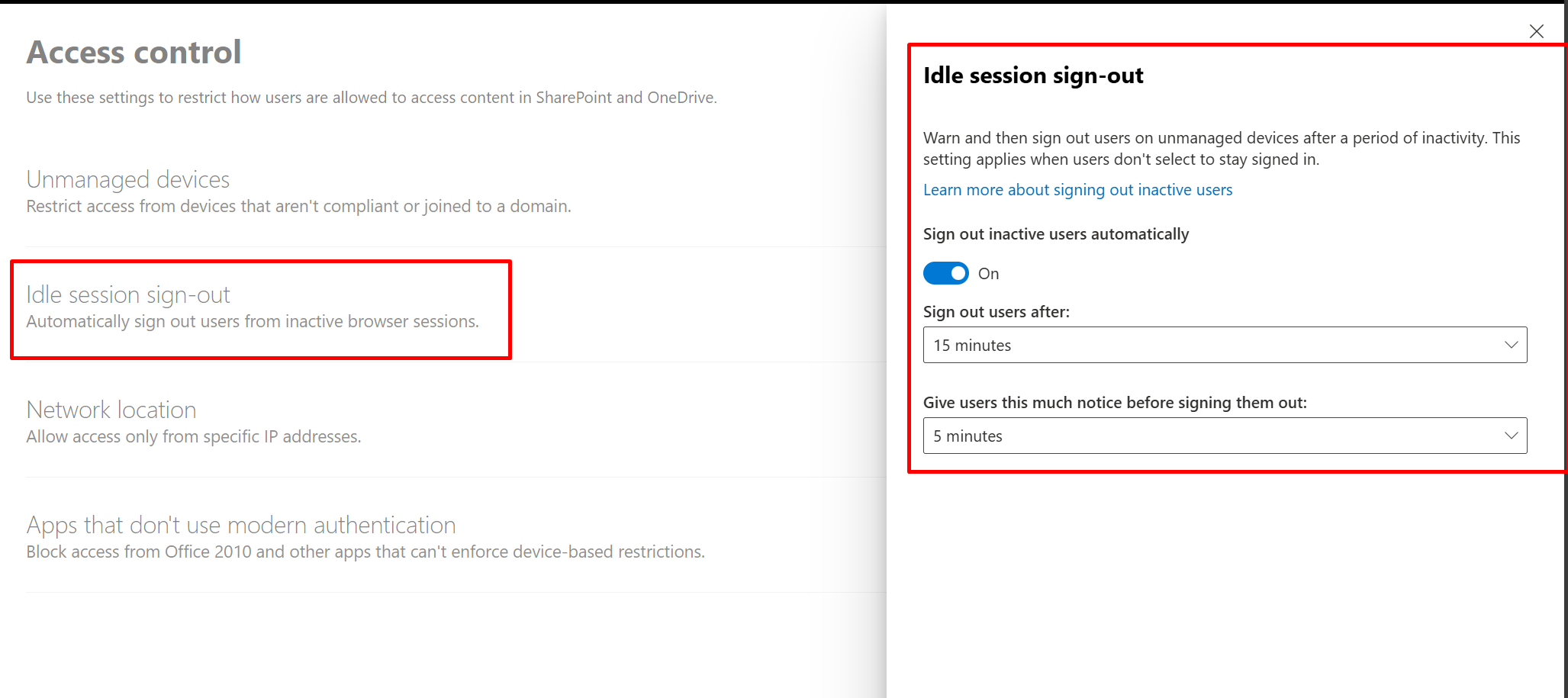
By defualt it creates 2 CA policies
Make sure to edit and just add groups you need and exclude your Global admin account
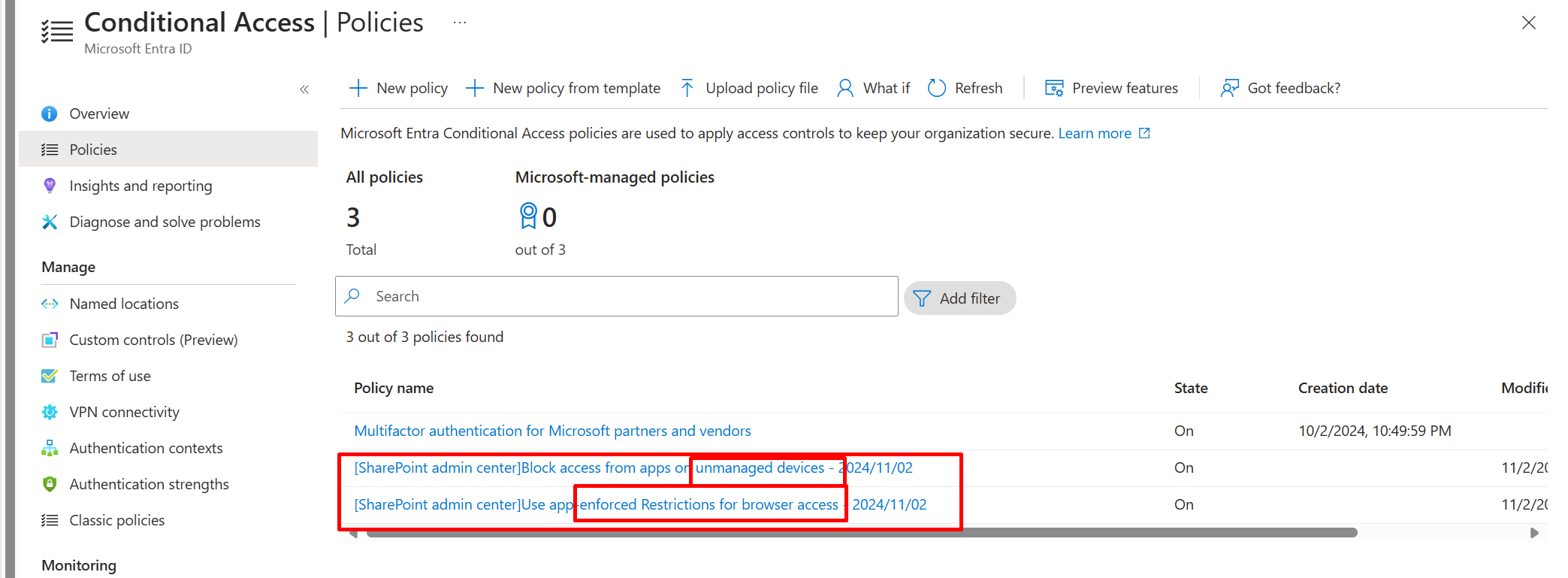
2 conditional access policies are created for all company one for compliant devices and other for
Browserfor in active or idle sessions
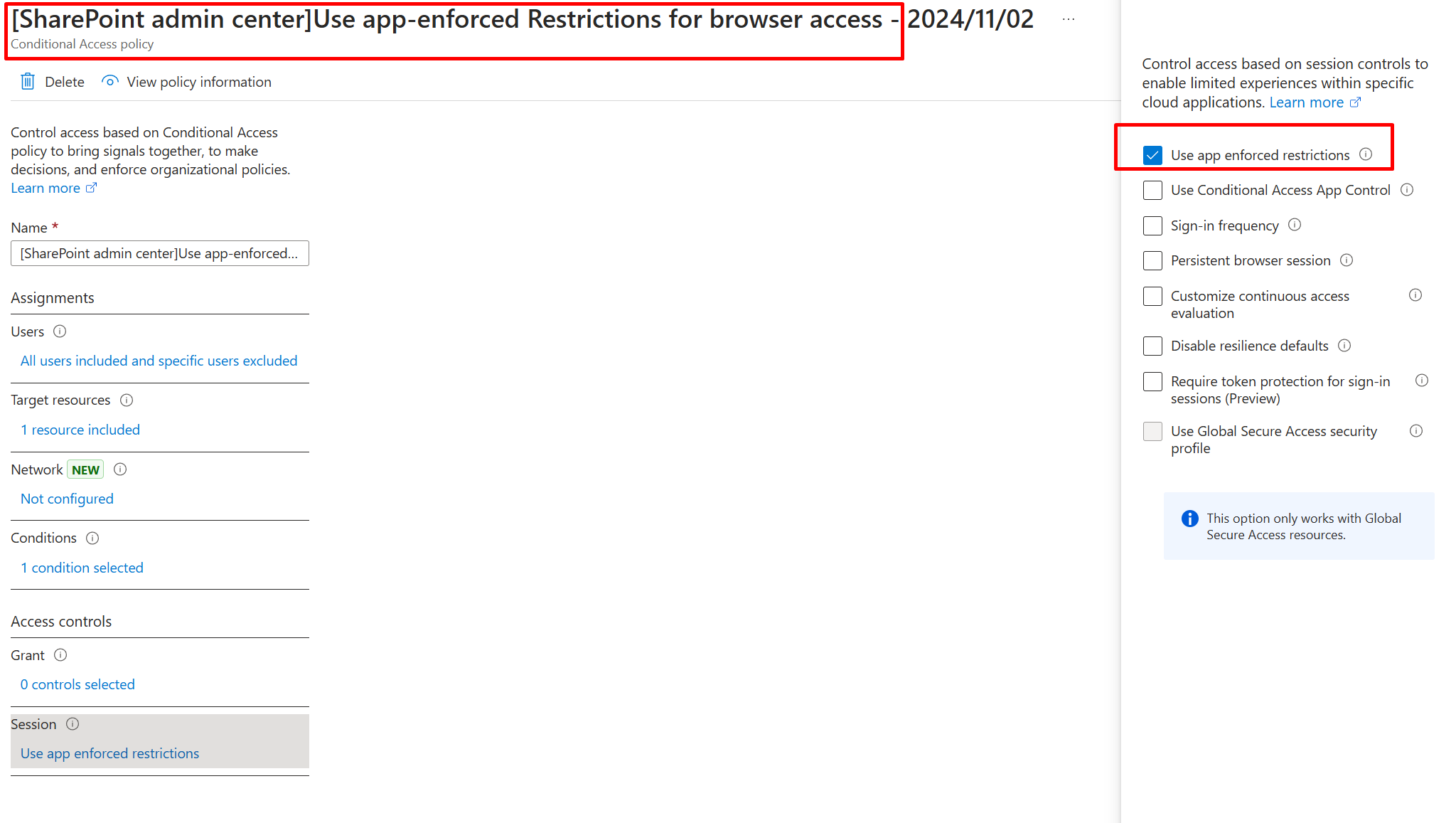
The following is how it is applied for 2 users included and other not included in policy:
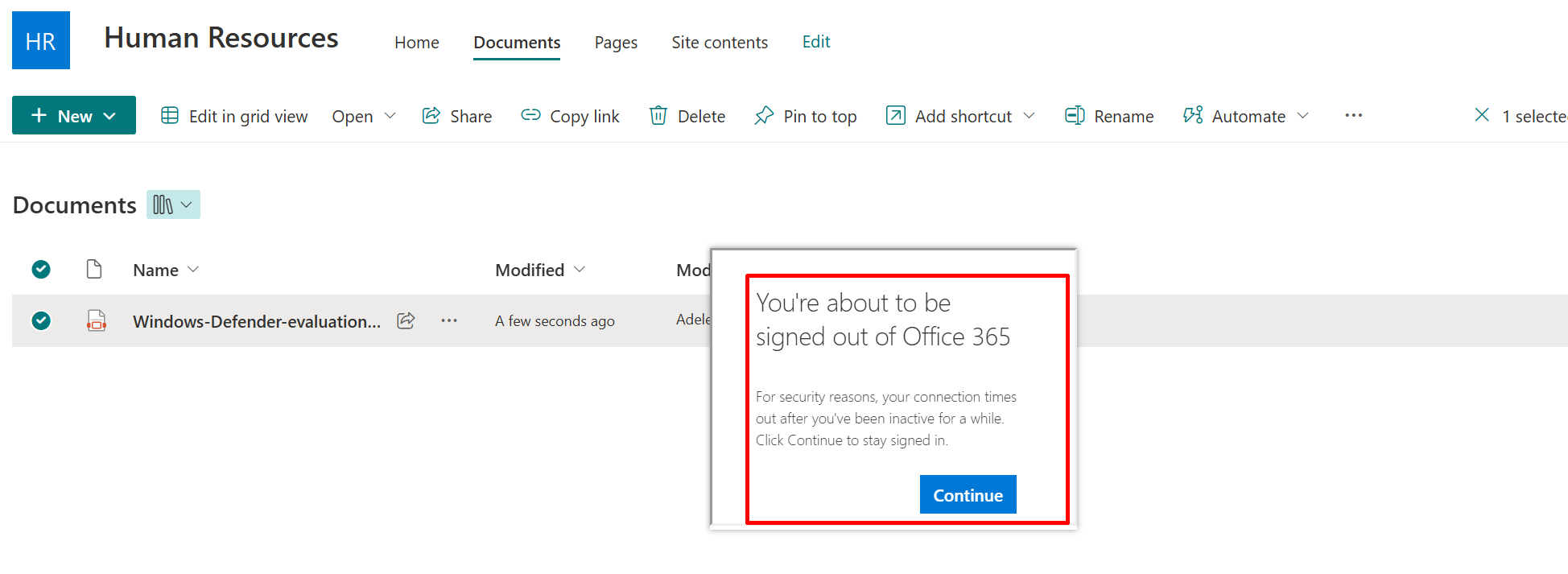
And for the idle session the users will receive
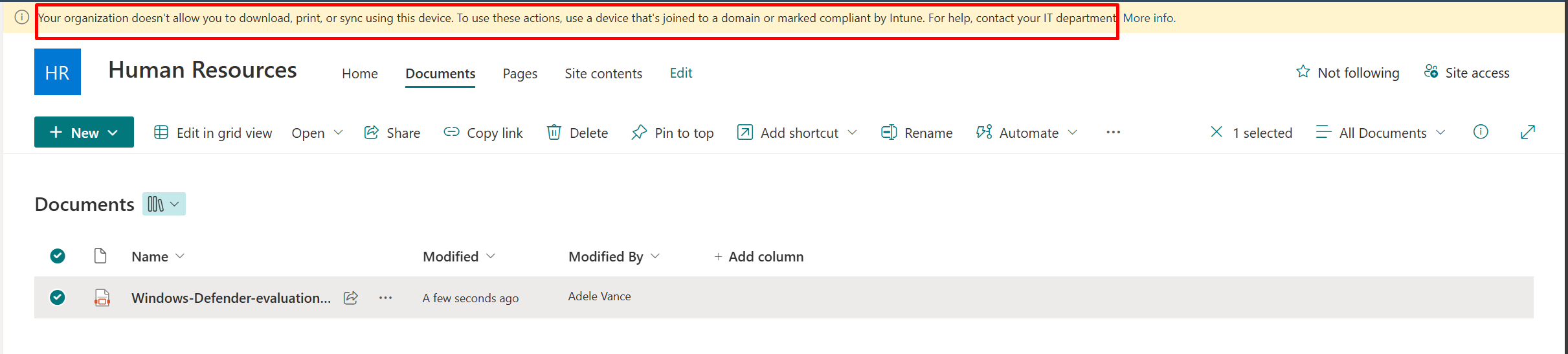
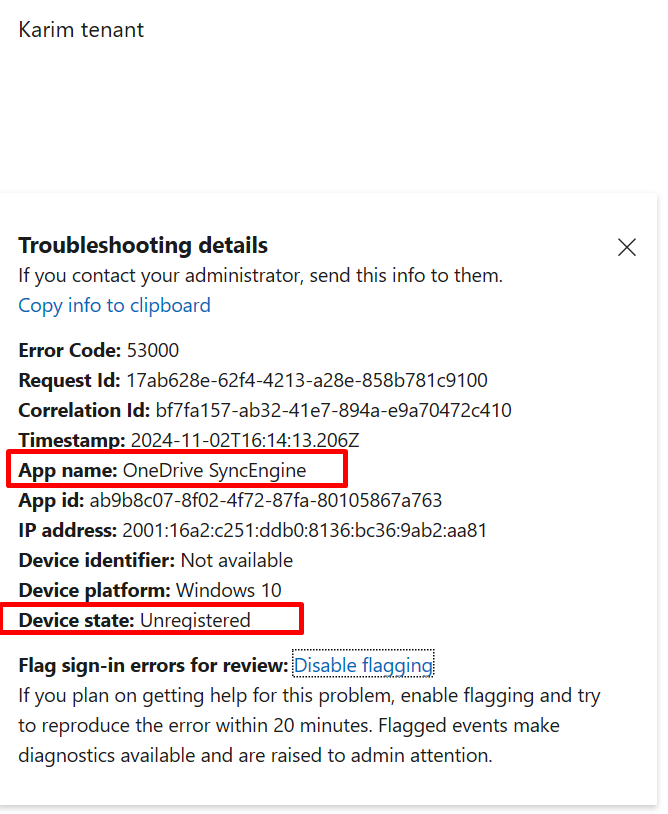
And this is for unmanaged device policy
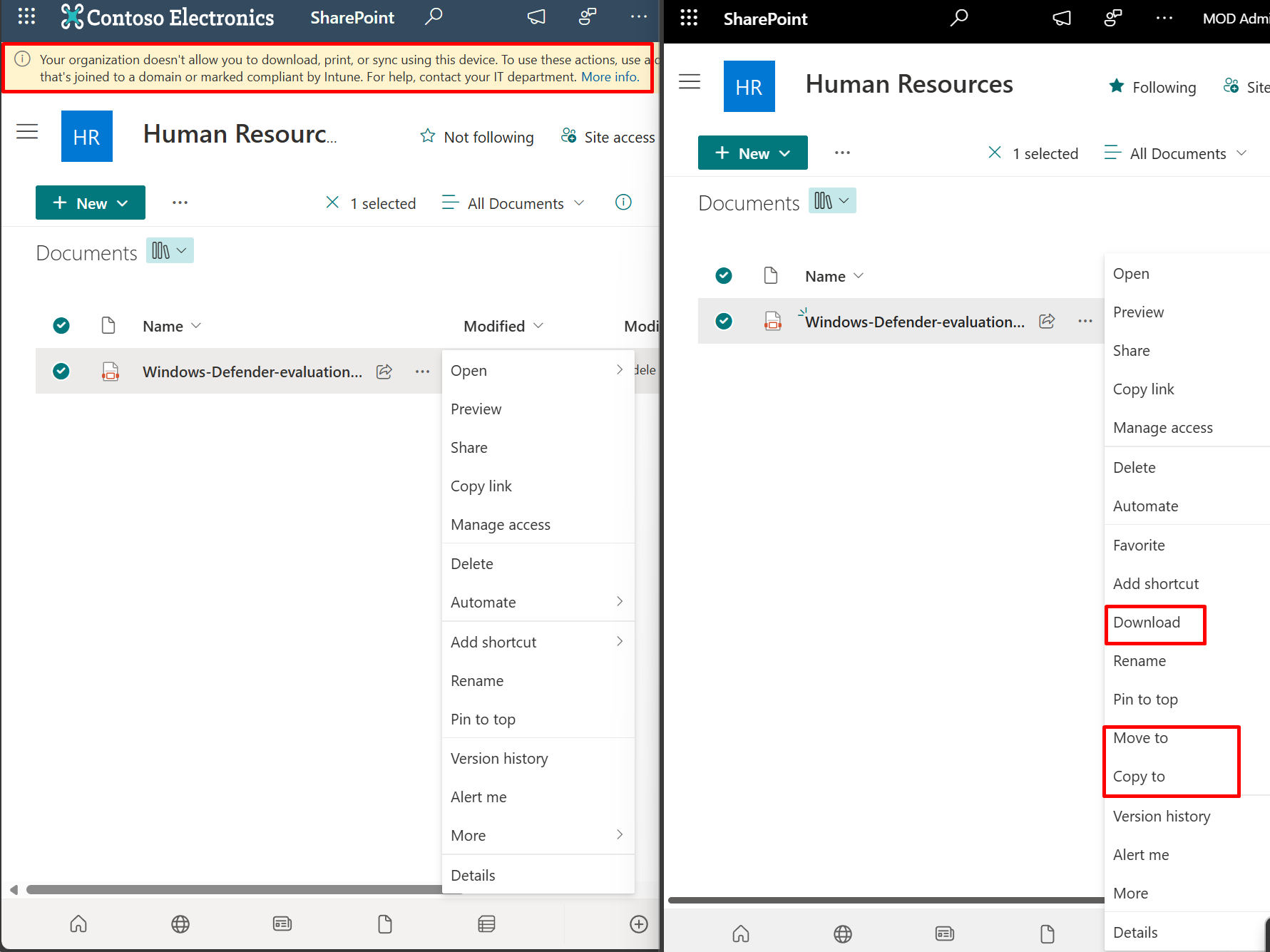
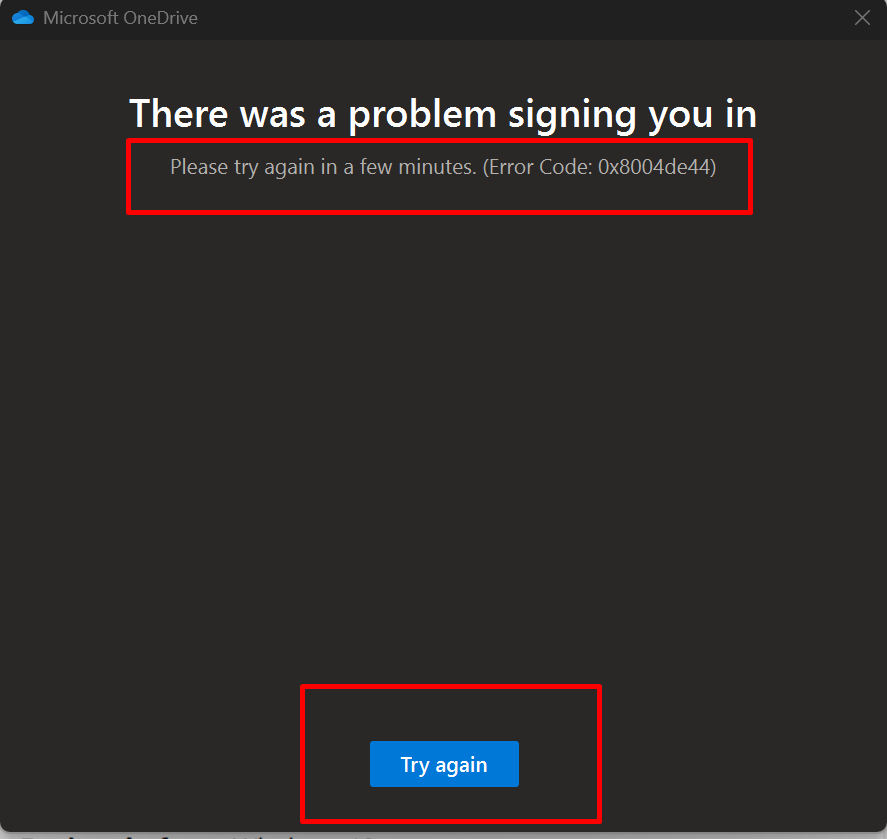
Now when the user tries to print or download or open in another App the following will be the behaviour

You must apply the Microsoft Single Sign On extension to google
If they get single sign-on (SSO) into the web app from the device joined account.
If they selected Stay signed in at the time of sign-in. For more info on hiding this option for your organization, see Add branding to your organization's sign-in page.
If they're on a managed device (one that is compliant or joined to a domain) and using a supported browser like Microsoft Edge or Google Chrome (with the Microsoft Single Sign On) extension.
Idle session timeout for Microsoft 365
Idle session timeout for Microsoft 365 - Microsoft 365 admin | Microsoft Learn