Hi everyone! As the title suggests, today’s blog is all about how to use Azure Active Directory App Proxy to enable secure remote access to your on-premises applications. Here are the key points that our blog will focus on:
- Zero Trust controls.
- Create Kerberos delegation.
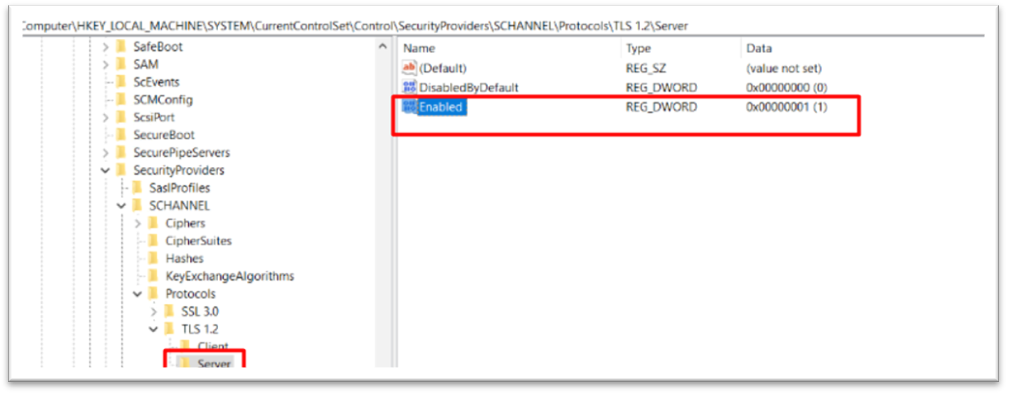
- Enable TLS 1.1 and TLS 1.2 from the registry
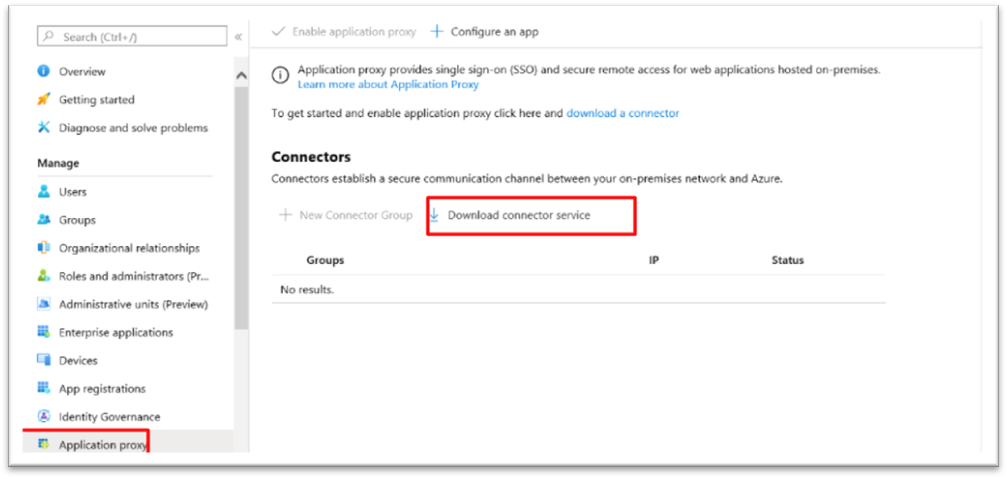
- Install the application Proxy.
- Configure the SSO.
- Prerequisites for SSO.
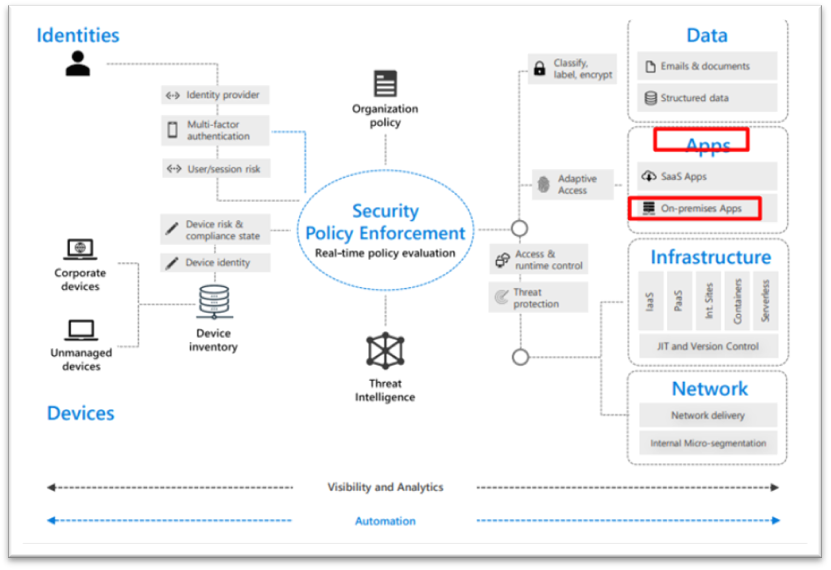
What is ZERO TRUST?
A Zero Trust strategy requires that you verify explicitly, use least privileged access principles, and assume breach. Azure Active Directory can act as the policy decision point to enforce your access policies based on user, device, target resource, and environment insights.
Zero Trust controls and technologies across six foundational elements:
- Identities
- Devices
- Applications
- Data
- Infrastructure
- Networks
Our blog discusses the Application element (on-Prem)
Integrate all your applications with Azure AD.
SSO is not only a convenient feature for users, but it is also a security posture, as it prevents users from leaving copies of their credentials in various apps and helps them avoid getting used to surrendering their credentials due to excessive prompting.
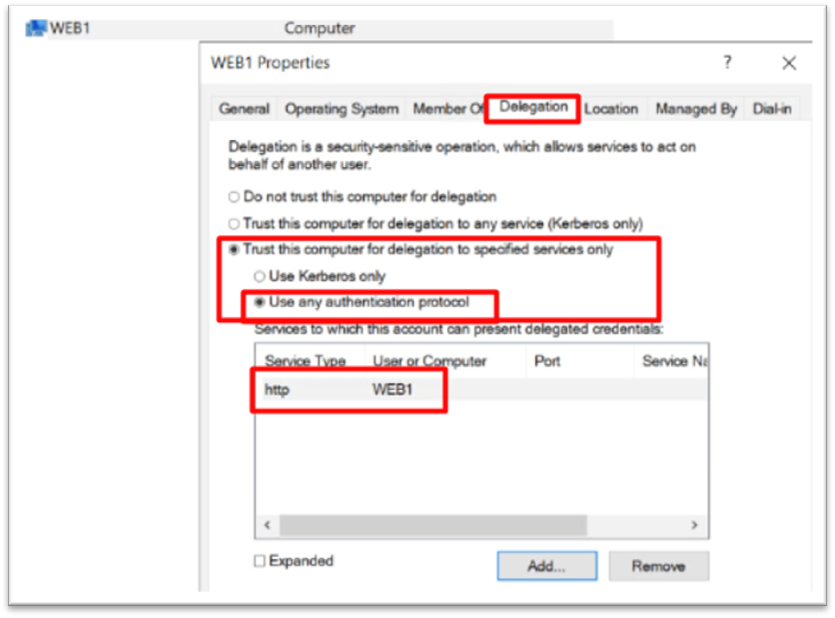
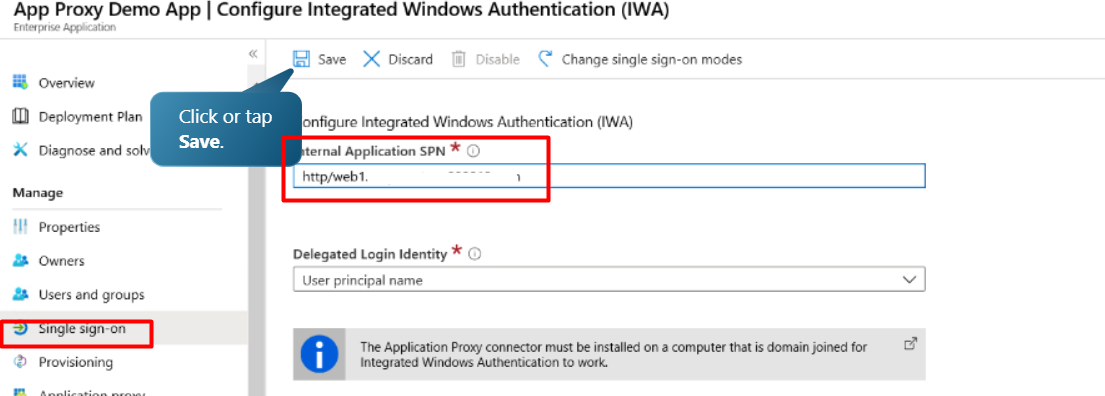
Create Kerberos delegation (SPN)
First, log in to on-prem Active directory, then go to the “Delegation” tap and add SPN to the required server.
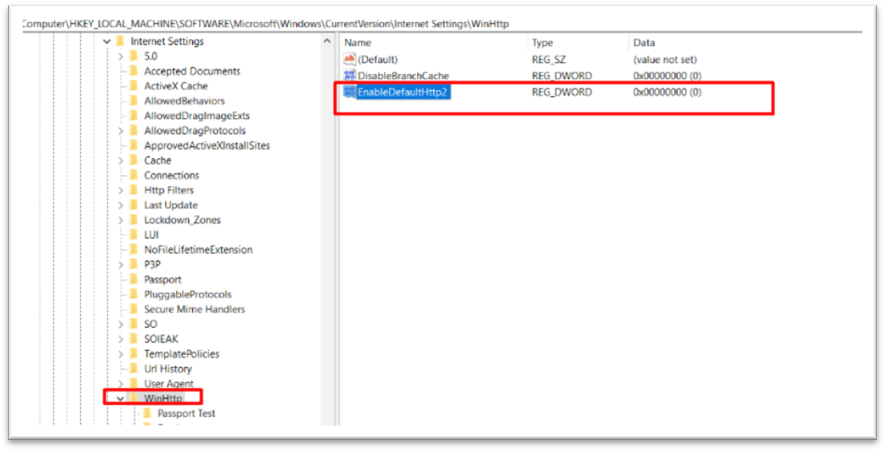
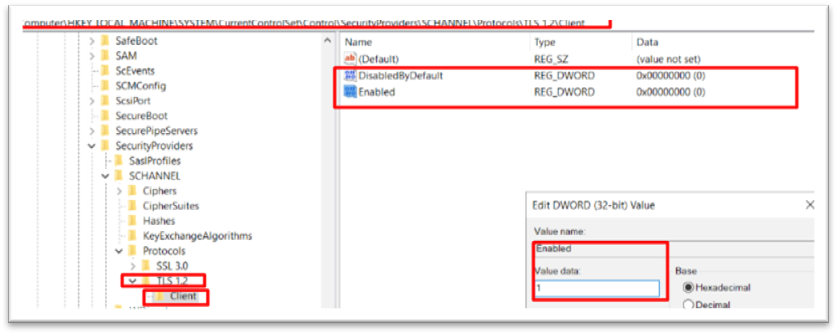
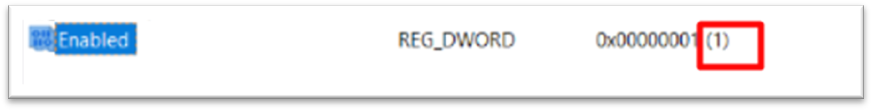
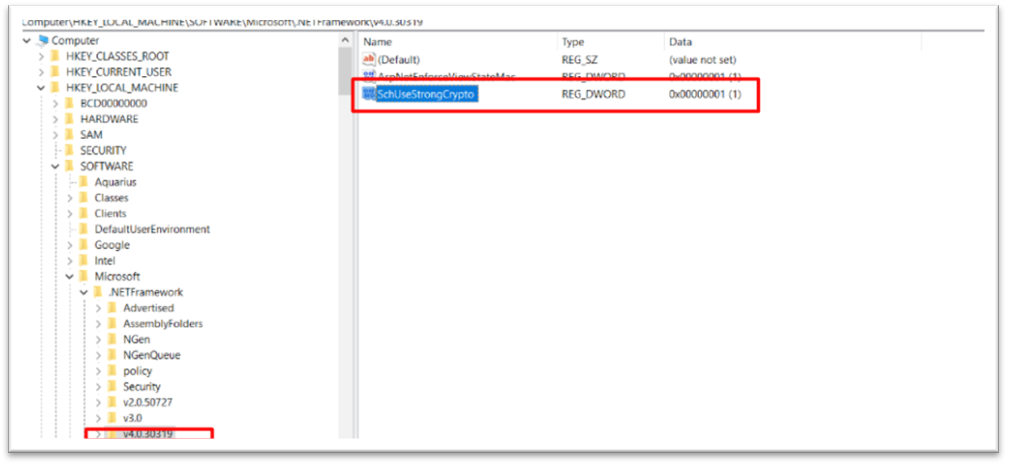
Create TLS 1.2 from registry
Then go to the registry as shown below.
Application Proxy in Azure Active Directory
Azure Active Directory (Azure AD) has an Application Proxy service that enables users to access on-premises applications by signing in with their Azure AD account.
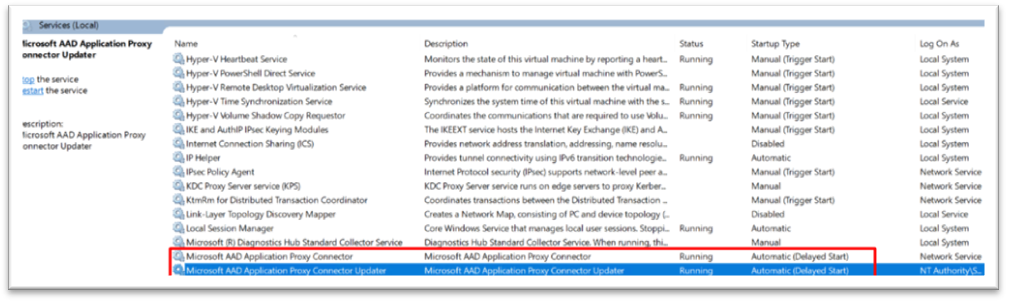
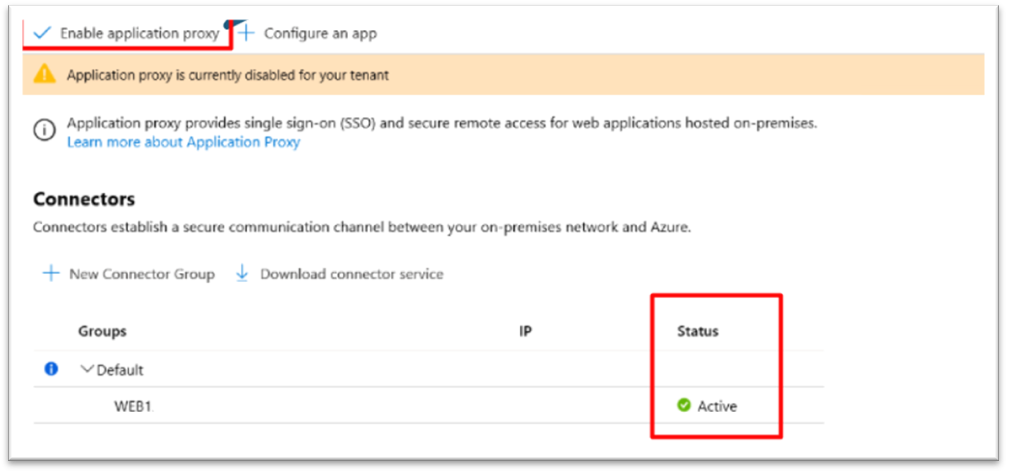
Both services must be running
Enable the Application Proxy
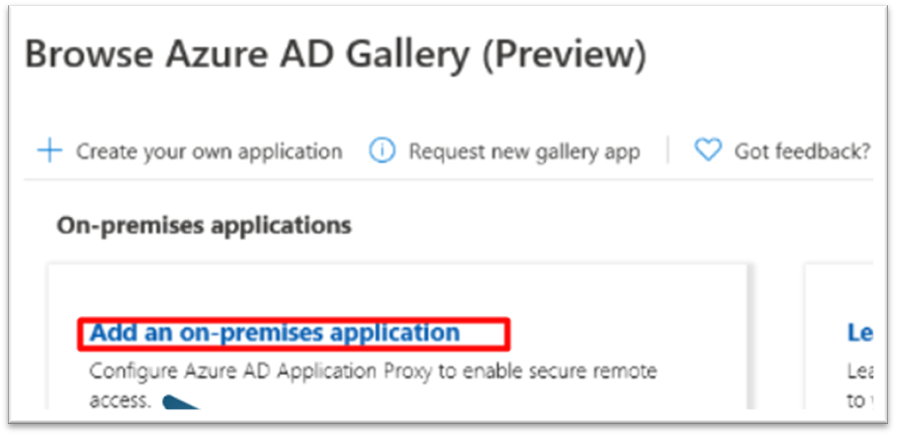
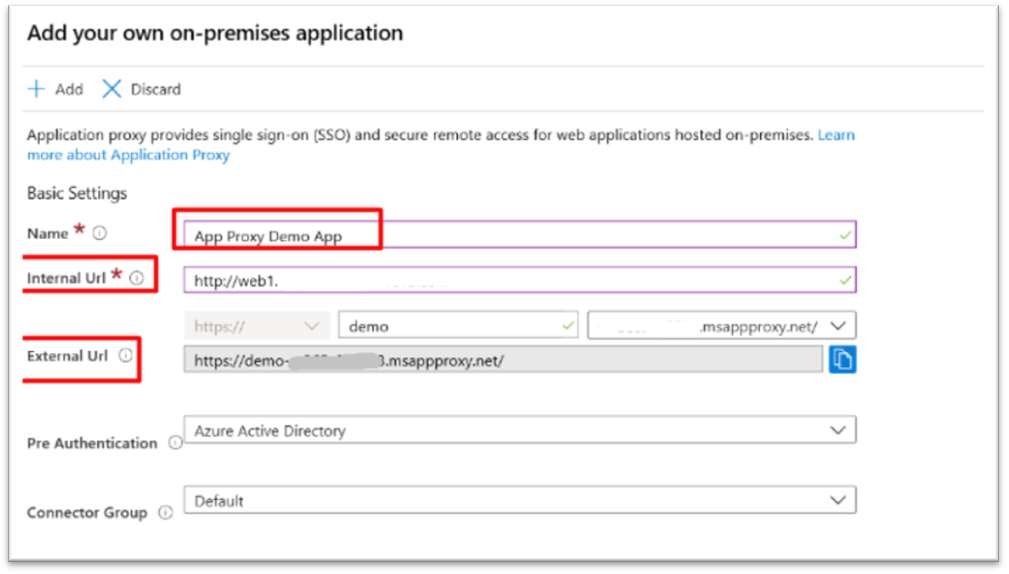
The next step is to go to enterprise application > Add new application > Add an on-premises application.
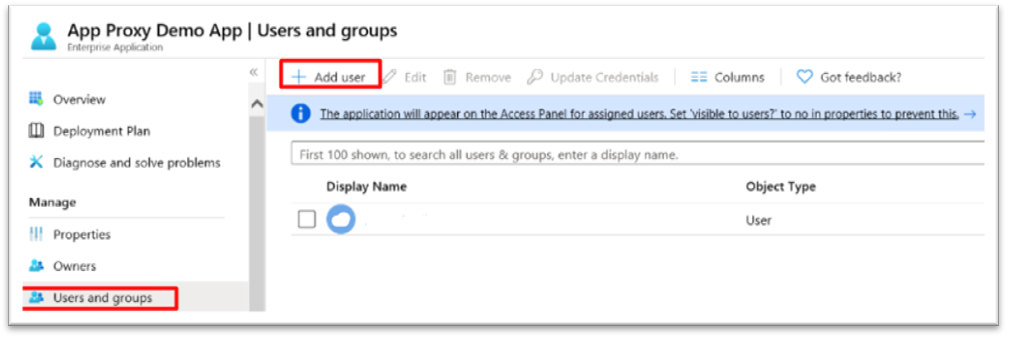
Add a user to the application.
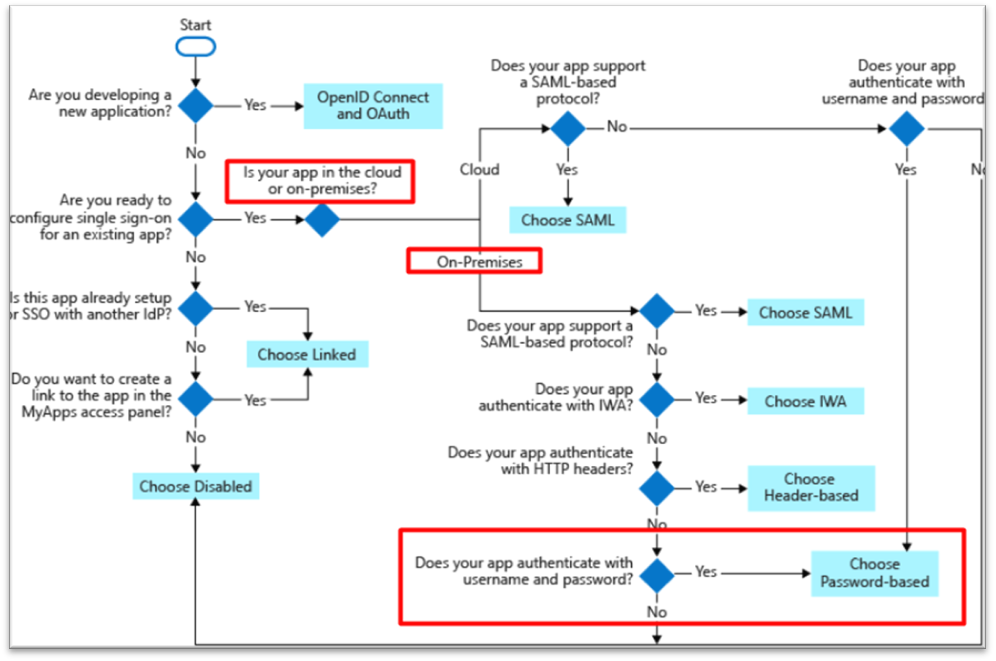
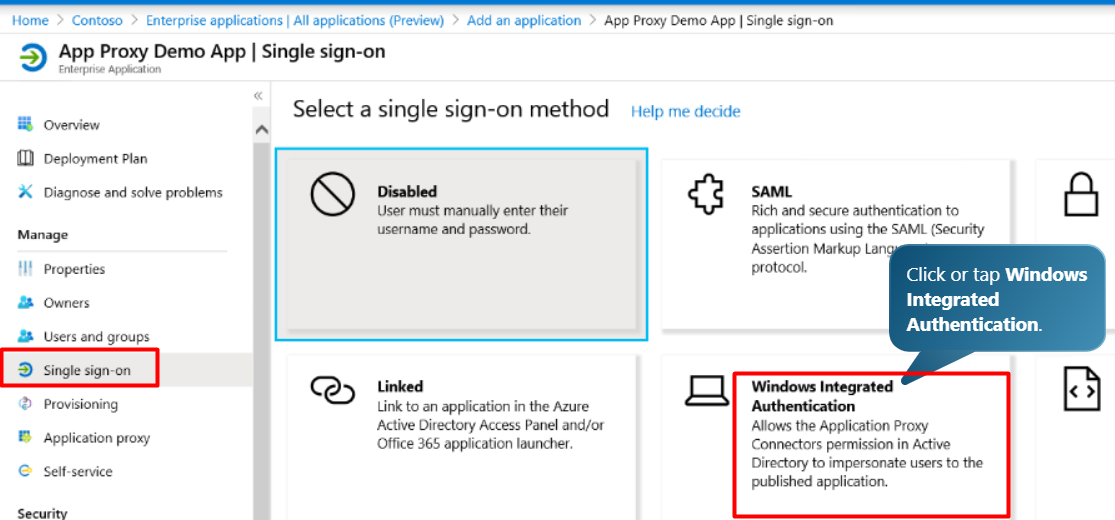
Choose the SSO method
According to the design of the application and what Authentication method is supported.
Configure the SSO.
We will use windows authentication method.
Blog written by: Karim A. Zaki
Ctelecoms Team
References